道德駭客實務入門-4/22課程筆記-3
TibaMe: 道德駭客實務入門及CEH認證班
Teacher: 林煌錡 (Alex Lin)
The class on 4/22 introduced wireless network hacking, mobile platform hacking, IOT hacking and cloud platform hacking, and cryptography. I separated the content into three parts. This note is about cryptography.
Part3: cryptography
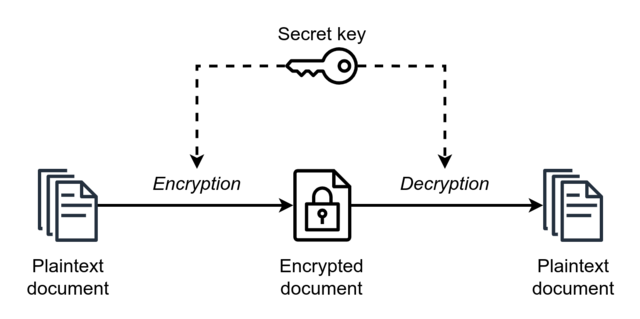
🔸 Symmetric Cryptography
From Wiki: https://en.wikipedia.org/wiki/Symmetric-key_algorithm
Algorithms
DES & 3DES
https://en.wikipedia.org/wiki/Data_Encryption_Standard
https://en.wikipedia.org/wiki/Triple_DES
AES 128/192/256
https://en.wikipedia.org/wiki/Advanced_Encryption_Standard
- Initialization vector (IV)
- Padding
- Block cipher mode
ECB / CBC / CFB / CTR / GCM / OFB / CFB
Stream Cipher
https://en.wikipedia.org/wiki/Stream_cipher
Operate on plaintext streams and generates a stream of key bits that are combined with the plaintext to produce the ciphertext. They are commonly used in applications where real-time encryption and decryption is required, such as in wireless communications and secure voice communication systems.
Use Cases
- Data Encryption
- File Protection
- Stream Encryption
🔸 Asymmetric Cryptography
From Wiki: https://en.wikipedia.org/wiki/Public-key_cryptography
Asymmetric cryptography takes longer time compared to symmetric cryptography.
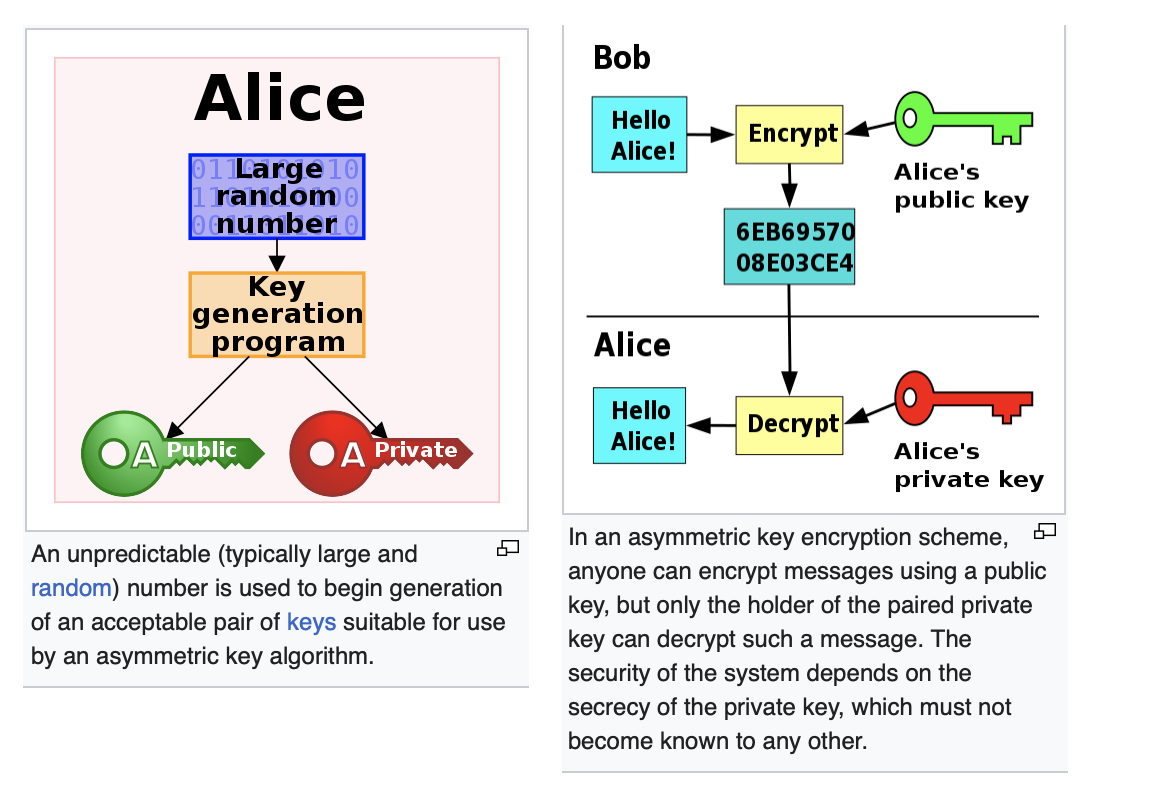
Algorithms
RSA
https://en.wikipedia.org/wiki/RSA_(cryptosystem)
RSA Padding:
- NoPadding
- PKCS1
- OAEP
- PSS
Elliptic Curve Cryptography (ECC)
https://en.wikipedia.org/wiki/Elliptic-curve_cryptography
Use Cases
HTTPS
SSL
- SSL 1.0
- SSL 2.0
- SSL 3.0
TSL
- TSL 1.0
- TSL 1.1
- TSL 1.2
- TSL 1.3
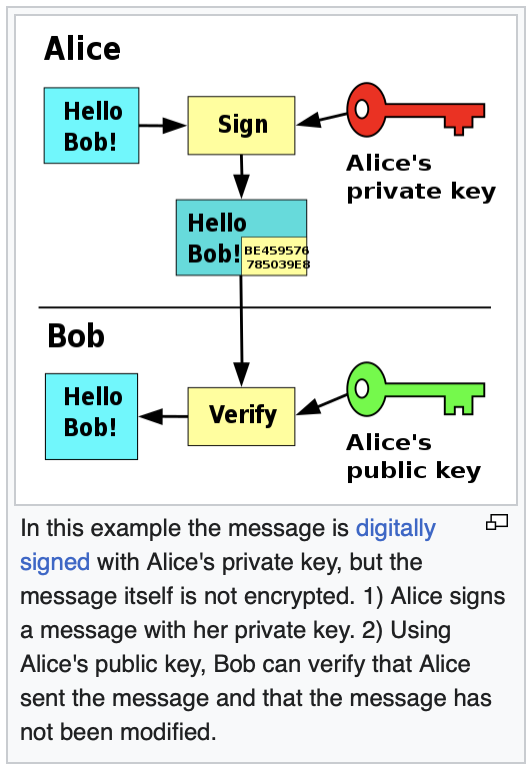
Digital Signatures
From Wiki
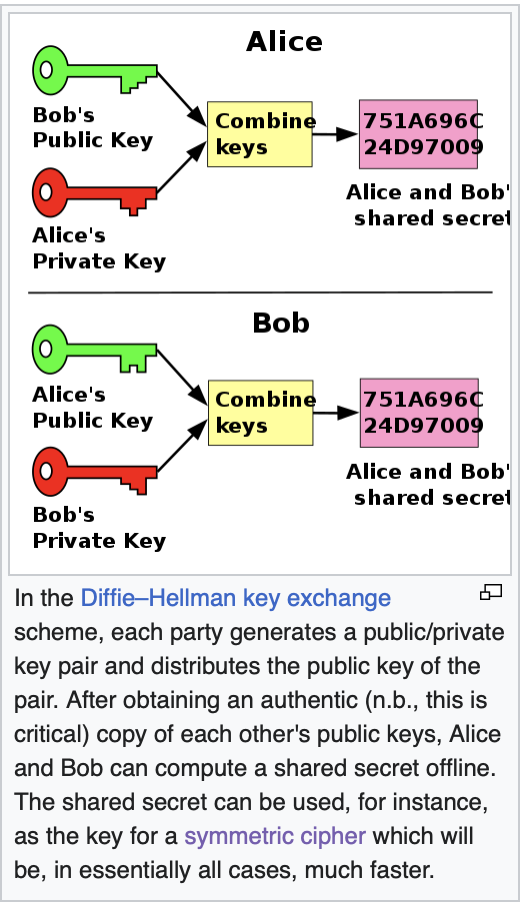
Key Exchange
From Wiki
Diffie-Hellman
Digital Certificates
A digital certificate is issued by a trusted third-party called a Certificate Authority (CA), which verifies the identity of the certificate holder and binds their public key to a unique identifier called a “subject.” This subject can be an individual, an organization, or a device, and is included in the digital certificate along with the public key.
Pretty Good Privacy (PGP)
https://zh.wikipedia.org/zh-tw/PGP
GNU Privacy Guard (GPG)
https://zh.wikipedia.org/zh-tw/GnuPG
Secure Email
In secure email, the sender uses the recipient’s public key to encrypt the message, which can only be decrypted using the recipient’s private key.
Blockchain
In a blockchain network, each participant has a unique public-private key pair, which they use to sign and verify transactions.
🔸 Hash
Input Message –> Hash Function –> Hashed Message
Algorithms
Message-Digest
MD5 (Has vulnerabilities)
https://zh.wikipedia.org/zh-tw/MD5SHA
https://zh.wikipedia.org/zh-hant/SHA家族
❌ SHA-0
❌ SHA-1
✅ SHA-2
✅ SHA-3
Use Cases
Data integrity: Hash functions can be used to verify the integrity of data, ensuring that it has not been modified or corrupted in transit. This is commonly used in digital signatures, where a hash of the message is signed using a private key to generate a digital signature that can be verified using a public key.
Password storage: Hash functions are often used to store passwords securely in a database. When a user creates a password, its hash is stored in the database instead of the plaintext password. When the user logs in, the system compares the hash of the entered password with the stored hash to verify the password.
Content addressing: Hash functions can be used to generate unique identifiers for files and other content. This allows content to be identified and shared without needing to store the entire file or content. This is commonly used in peer-to-peer file sharing networks and content distribution systems.
Message authentication: Hash functions can be used to generate message authentication codes (MACs) that can be used to authenticate messages and ensure that they have not been tampered with in transit.
Blockchain: Hash functions are a fundamental component of blockchain technology. In a blockchain, each block contains a hash of the previous block, forming a chain of blocks. This allows the integrity of the blockchain to be verified by checking the hashes of each block in the chain.
🔸 HMAC
HMAC is used for message authentication, integrity, and secrecy. HMAC includes a secret key in the computation, which allows it to provide both integrity and authenticity of a message.
From Alex Xu’s blog: https://blog.bytebytego.com/p/how-to-design-a-secture-web-api-access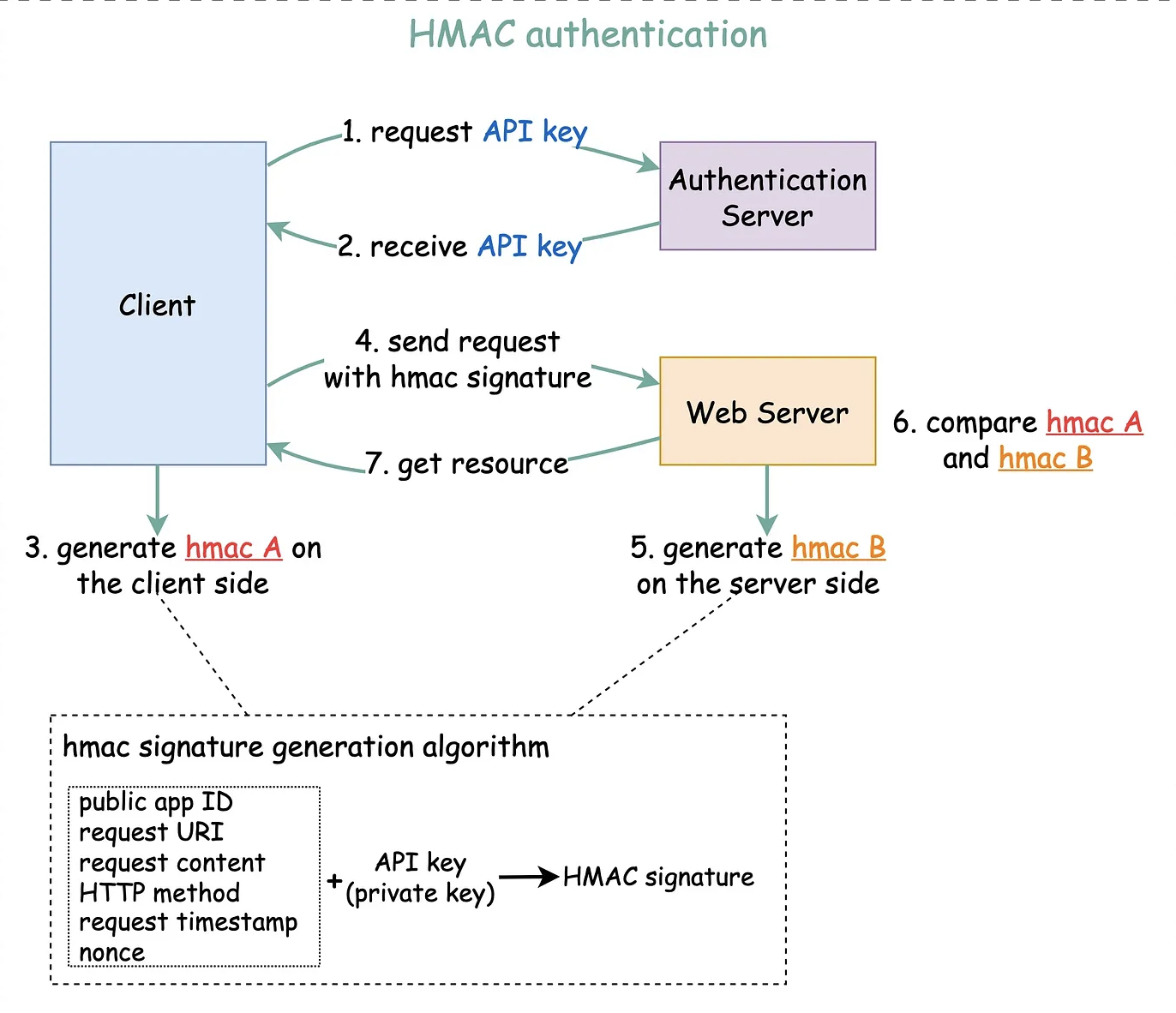
🔸 Tools
CyberChef
Can carry out all manner of “cyber” operations within a web browser.
https://github.com/gchq/CyberChef
👉 https://gchq.github.io/CyberChef/#recipe=MD5()&input=ampqamtraw
OpenSSL
https://zh.wikipedia.org/zh-tw/OpenSSL
https://www.openssl.org
RSACTFTool
https://github.com/RsaCtfTool/RsaCtfTool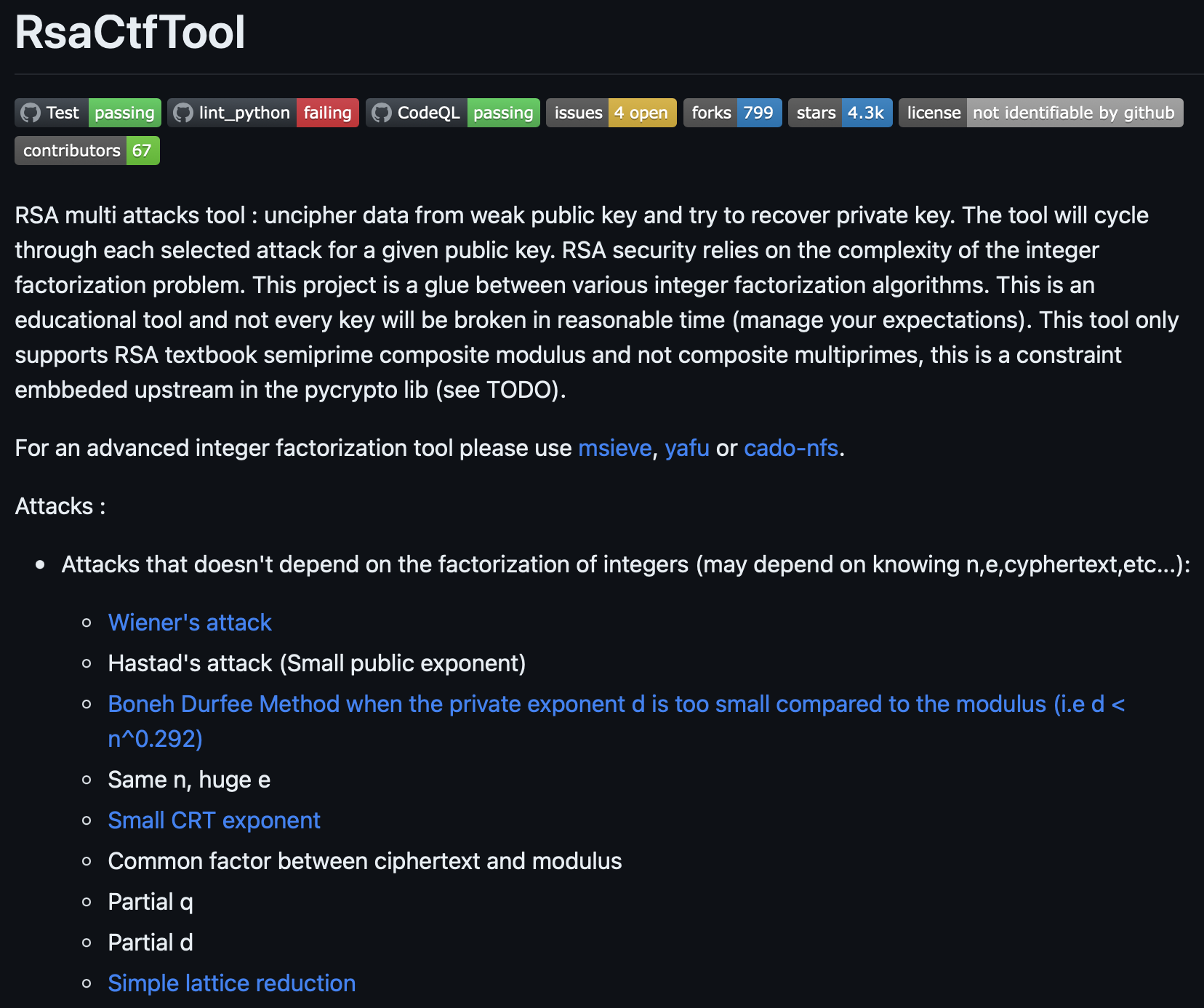
CrypToll
https://en.wikipedia.org/wiki/CrypTool
https://www.cryptool.org
Hard Disk Encryption Tools
Windows BitLocker
BitLocker is a built-in disk encryption tool that comes with Windows 10 Professional and Enterprise editions. It can encrypt entire drives or individual files and folders, and supports several encryption modes, including AES-CBC and XTS-AES.
https://en.wikipedia.org/wiki/BitLocker
VeraCrypt
VeraCrypt is a free, open-source disk encryption software that can encrypt entire partitions or drives. It supports multiple encryption algorithms, including AES, Serpent, and Twofish, and can create hidden volumes for added security.
https://en.wikipedia.org/wiki/VeraCrypt
DiskCryptor
DiskCryptor is a free, open-source disk encryption tool that supports multiple encryption algorithms, including AES, Twofish, and Serpent. It can encrypt entire disks or individual partitions and supports both BIOS and UEFI firmware.
Symantec Endpoint Encryption
Symantec Endpoint Encryption is a commercial disk encryption tool that provides full-disk encryption for Windows and Mac systems. It uses strong encryption algorithms, including AES-256, and can integrate with Active Directory for easier management.
FileVault
FileVault is a built-in disk encryption tool that comes with macOS. It can encrypt the entire startup disk or just the user’s home folder and supports both AES-XTS and AES-CBC encryption modes.
🔸 Public Key Infrastructure (PKI)
PKI Wiki: https://en.wikipedia.org/wiki/Public_key_infrastructure
- 憑證管理系統(Certificate Management System)
- 憑證機構(Certification Authority ,CA)
- 註冊中心(Register Authority ,RA)
- 數位憑證(Digital Certificates)
- 驗證中心(Validation Authority ,VA)
From Teacher Alex’s PPT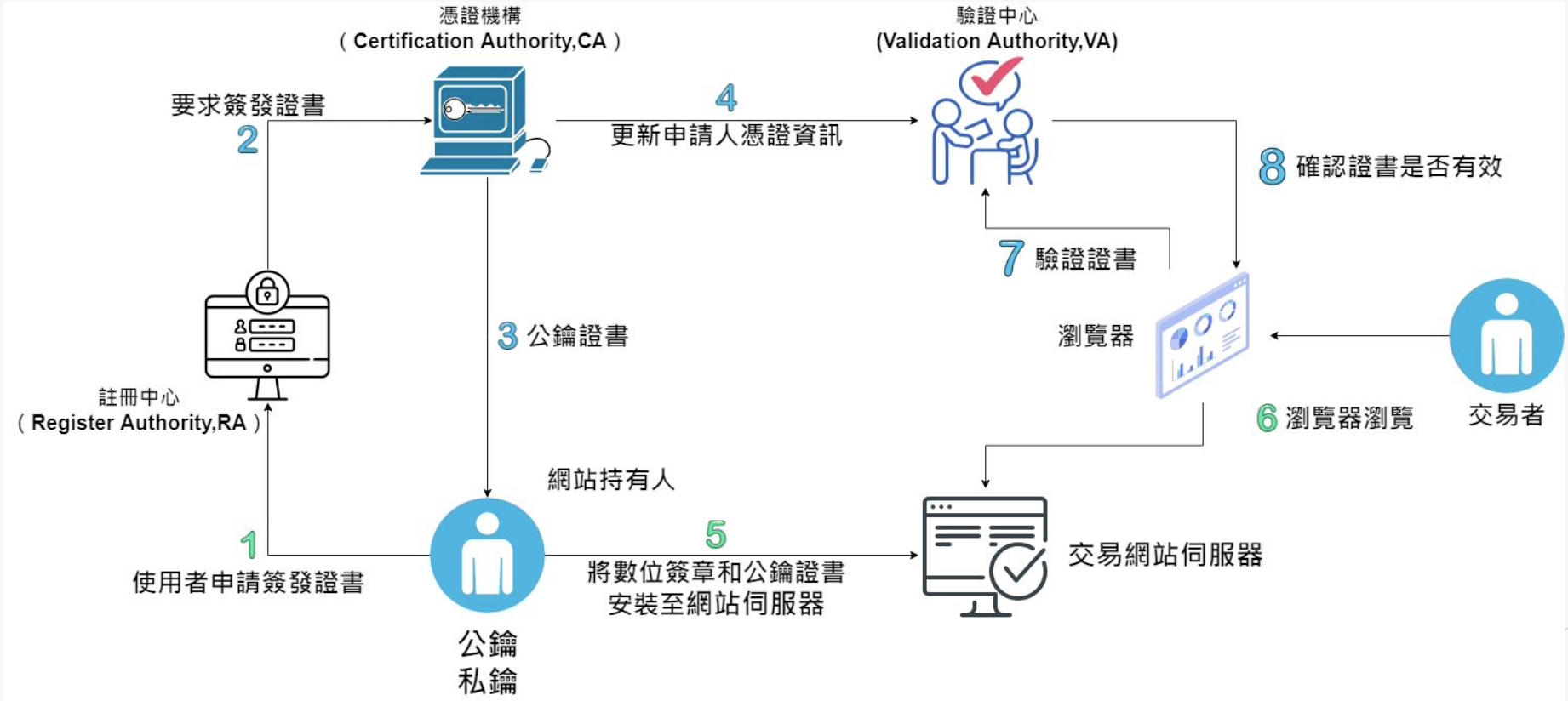
🔸 Attack Methods
Hard Code Attack
A hard-coded attack, also known as a hard-coded password attack, is a type of vulnerability exploitation where an attacker gains unauthorized access to a system or application by exploiting a hard-coded password that is stored in the code or configuration files.
Prevention:
- Avoid hard-coding passwords and instead store them in secure configuration files or databases, using strong encryption and hashing techniques.
Rainbow Table Attack
A Rainbow Table attack is used to crack hashed passwords.
Rainbow Table attacks work by precomputing a large number of hashes and storing them in a lookup table, known as a Rainbow Table. The Rainbow Table contains a list of possible passwords and their corresponding hashes. When an attacker obtains a hashed password, they can then compare it against the entries in the Rainbow Table to find a match. If a match is found, the corresponding password is the plaintext equivalent of the hashed password.Rainbow Table attacks can be effective against weak passwords, as well as against poorly implemented hashing algorithms.
Prevention:
- Use strong and complex passwords, and to use secure hash functions that are resistant to precomputation attacks.
Related-key Attack
A related-key attack is a type of cryptographic attack that exploits a weakness in a cryptosystem when multiple keys are used that are related in some way, such as being generated from the same source or using the same algorithm.
Prevention:
Use cryptographically secure key generation methods, such as using true random number generators or hardware security modules (HSMs), which can generate independent keys that are not related to each other.
Use multiple independent keys for different operations, such as encryption and authentication.
Padding Oracle Attack
In a Padding Oracle Attack, an attacker submits an encrypted message to a server and monitors the response. The server may provide different responses depending on whether the padding in the message is valid or not. By repeatedly submitting modified versions of the message and observing the server’s response, an attacker can determine the correct padding and gradually decrypt the message.
Prevention:
- Use secure cryptographic protocols.
- Avoid exposing sensitive information through error messages or other feedback mechanisms.
DROWN Attack
The attack exploits a weakness in the SSLv2 protocol, which is an outdated and insecure version of the SSL/TLS protocol used for secure communications over the internet. Even though SSLv2 has been deprecated for many years, some servers still support it, leaving them vulnerable to the DROWN attack.
Prevent:
- Disable SSLv2 support on the servers.
Brute-force attack
- Symmetric Encryption
Below is from Teacher Alex’s PPT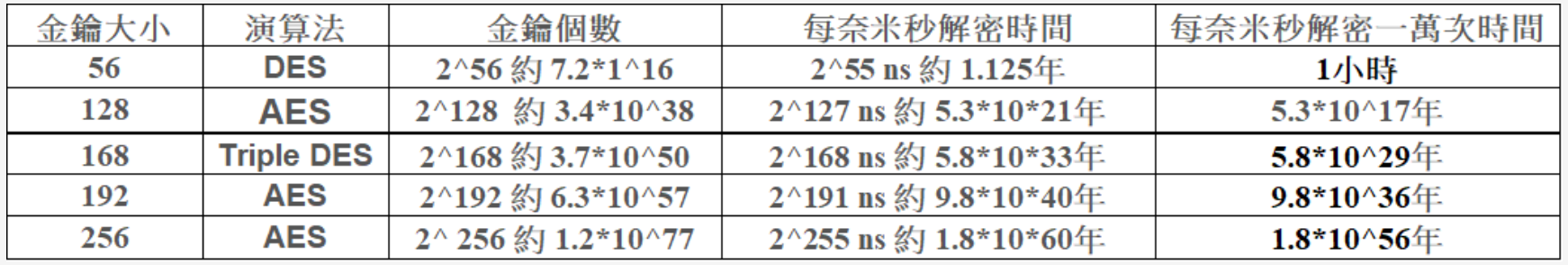
- Password
Below is from: https://uwnthesis.wordpress.com/2020/07/01/brute-force-password-how-long-will-it-take-to-brute-force-a-password/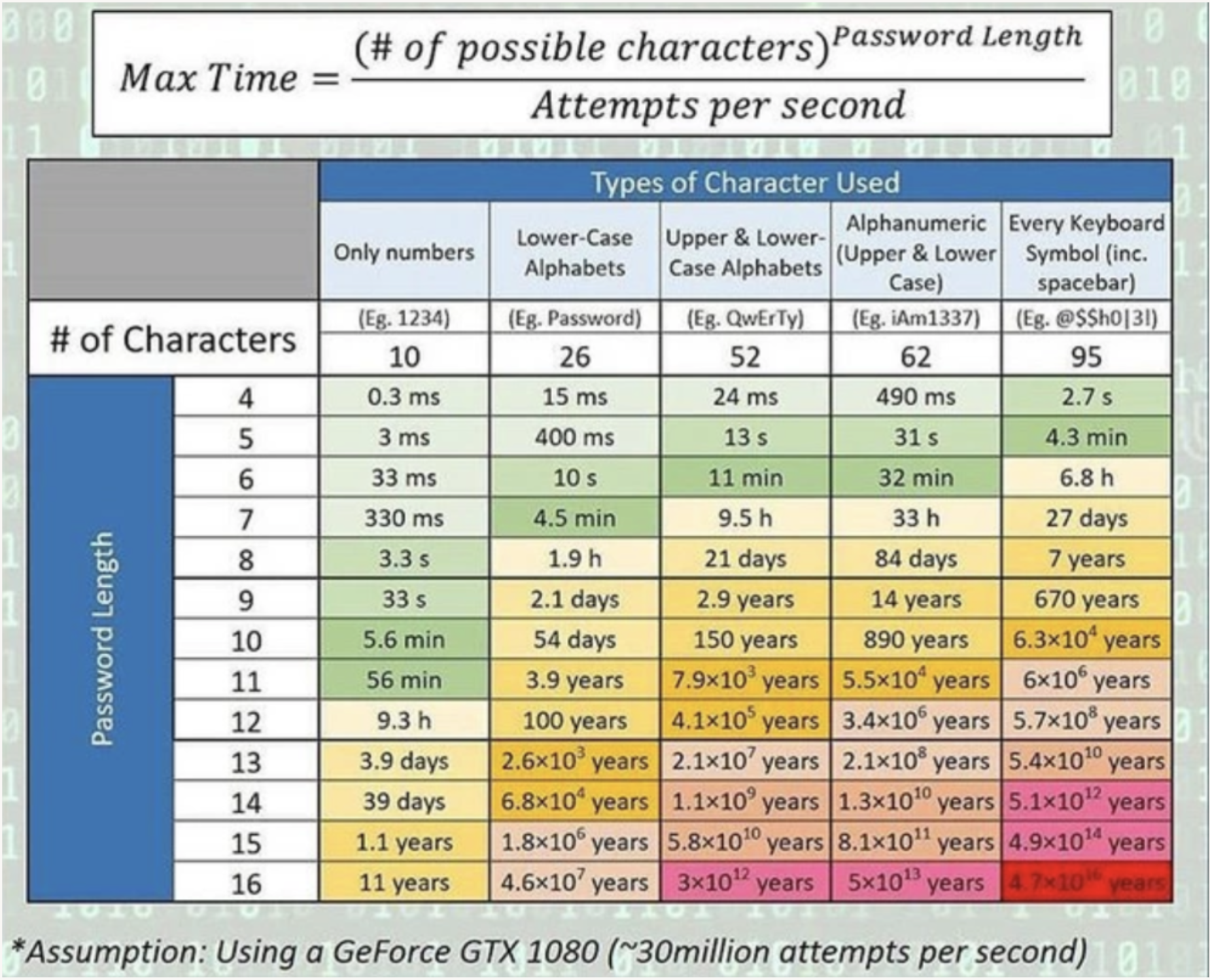
🔸 Hacking Case Studies
ZeroLogon
From Teacher Alex’s PPT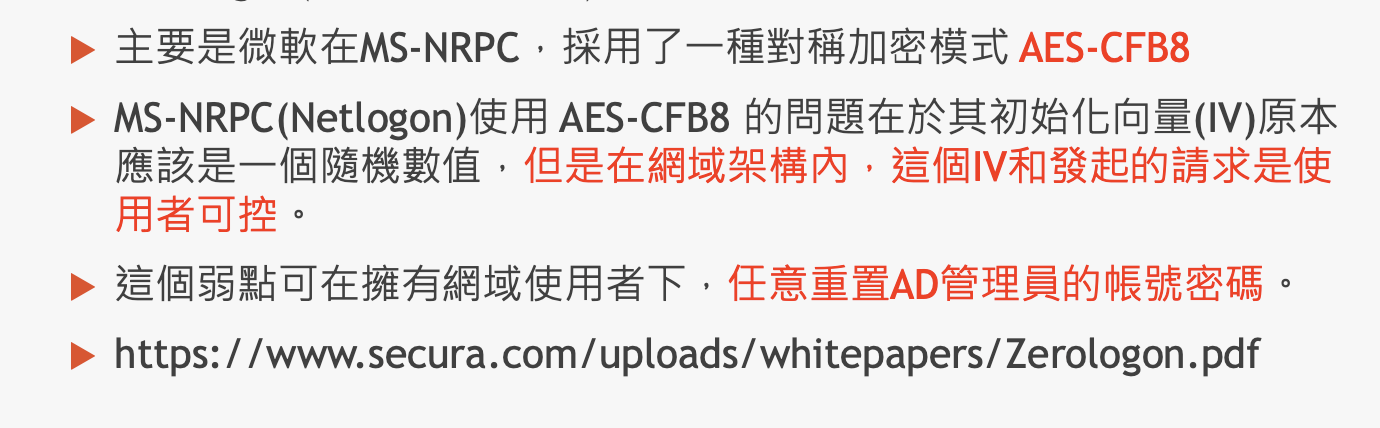
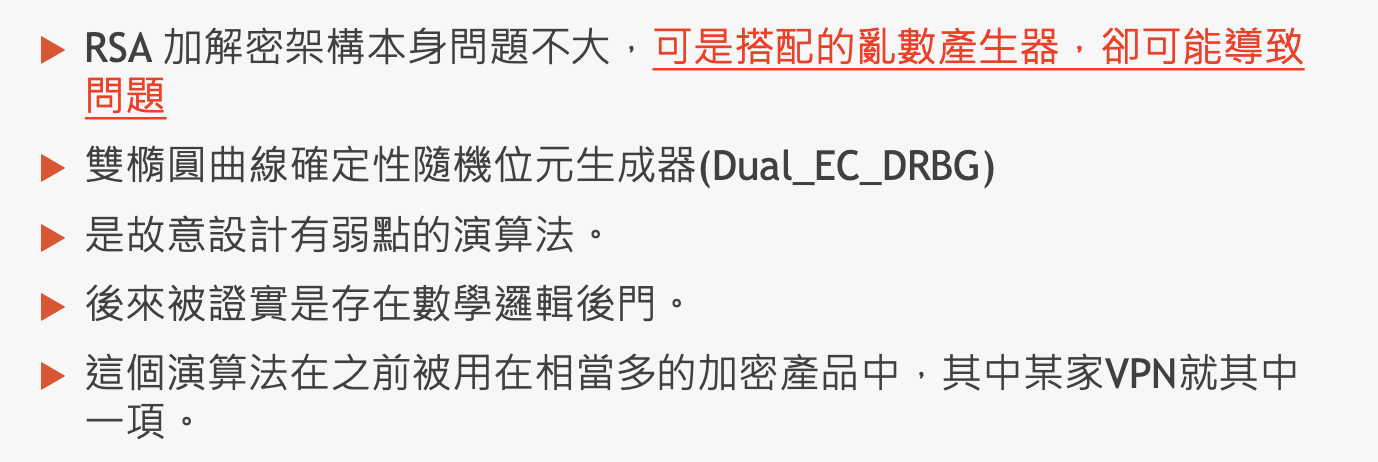
Dual_EC_DRBG
From Teacher Alex’s PPT