道德駭客實務入門-4/22課程筆記-1
TibaMe: 道德駭客實務入門及CEH認證班
Teacher: 林煌錡 (Alex Lin)
The class on 4/22 introduced wireless network hacking, mobile platform hacking, IOT hacking and cloud platform hacking, and cryptography. I separated the content into three parts. This note is about wireless network, IOT and cloud platform hacking.
Part1: Hacking wireless network, IOT and cloud platform
🔸 Wireless Network Hacking
WEP, WPA, WPA2 & WPA3
❌ WEP was the first security protocol developed for wireless networks. It uses a shared key to encrypt data transmitted over the wireless network. However, it has several vulnerabilities and is no longer considered secure.
❌ WPA was developed to address the vulnerabilities of WEP. It uses a stronger encryption algorithm called Temporal Key Integrity Protocol (TKIP) to encrypt data transmitted over the wireless network. It also provides a mechanism for authentication and key management. WPA is considered a more secure protocol than WEP, but it is still vulnerable to certain attacks.
✅ WPA2 is an improvement over WPA and is currently the most widely used security protocol for wireless networks. It uses Advanced Encryption Standard (AES) to encrypt data transmitted over the wireless network. It also provides a more secure mechanism for authentication and key management. WPA2 is considered a strong security protocol and is recommended for securing wireless networks.
✅ WPA3 is the latest security protocol for wireless networks. It was developed to address the vulnerabilities of WPA2 and provide even stronger security. It uses Simultaneous Authentication of Equals (SAE), a stronger key exchange protocol, to provide better protection against password-guessing attacks. It also provides improved encryption and protects against certain attacks like packet sniffing. WPA3 is considered the most secure protocol for wireless networks, but it is not yet widely adopted.
Attacks
- Rogue Access Point (RAP)
A Rogue Access Point (RAP) is an unauthorized wireless access point that is installed on a network without the knowledge or approval of the network administrator. RAPs are often installed by attackers or rogue employees to gain unauthorized access to a network or to eavesdrop on network traffic.
A RAP can be set up in a few different ways. For example, an attacker might bring their own wireless access point and connect it to the network, or they might use a wireless-enabled device such as a laptop or smartphone to create an ad-hoc network that other devices can connect to.
Once a RAP is set up, it can be used to intercept network traffic, steal sensitive information, or launch attacks against other devices on the network. RAPs can also be used to create “man-in-the-middle” attacks, where the attacker intercepts and modifies network traffic to steal data or launch additional attacks.
Teacher Alex mentioned Strip SSL here.
SSL stripping is a type of attack where an attacker intercepts communication between a web server and a client, and downgrades the secure HTTPS connection to an insecure HTTP connection.
- aLTEr(Long Term Evolution) Attack
In an aLTEr attack, the attacker first sets up a rogue base station, also known as an IMSI catcher or fake cell tower, to mimic a legitimate LTE network. The attacker can then use this fake network to intercept and modify the communication between the user’s device and the legitimate LTE network.
By intercepting the user’s traffic, the attacker can steal sensitive information such as login credentials, personal data, and financial information. The attacker can also modify the user’s traffic to inject malware or perform phishing attacks.
From Teacher Alex’s PPT: aLTEr attack 至少需在受害者附近架設一台將近2000美元的基地台,才有可能誘使受害者使用惡意的基地台。
- Key Reinstallation Attack (KRACK)
The attack takes advantage of a weakness in the WPA2 protocol that allows an attacker to reuse a cryptographic key that has already been used before, allowing the attacker to decrypt and manipulate the traffic between the client and the network. This can allow the attacker to inject malware, steal data, or modify data.
To prevent KRACK attacks, it is important to update all Wi-Fi devices to the latest firmware or software updates that fix the vulnerability. Additionally, using a Virtual Private Network (VPN) or other secure communication channel can help to protect against KRACK attacks by encrypting all network traffic. It is also important to avoid using public Wi-Fi networks for sensitive transactions, such as banking or shopping, as they are more vulnerable to KRACK attacks.
Jamming Signal Attacks
Denial-of-Service Attack
Wormhole Attack
Sinkhole Attack
Tools
WiGLE
WiGLE (or Wireless Geographic Logging Engine) is a website for collecting information about the different wireless hotspots around the world.
Wiki: https://en.wikipedia.org/wiki/WiGLE
https://wigle.net
Tools provided in Kali Linux.
- Fern Wifi Cracker
- Kismet
- GISKismet
- Ghost Phisher
- Wifite
🔸 IOT Hacking
IoT OWASP Top10
https://wiki.owasp.org/index.php/OWASP_Internet_of_Things_Project#tab=IoT_Top_10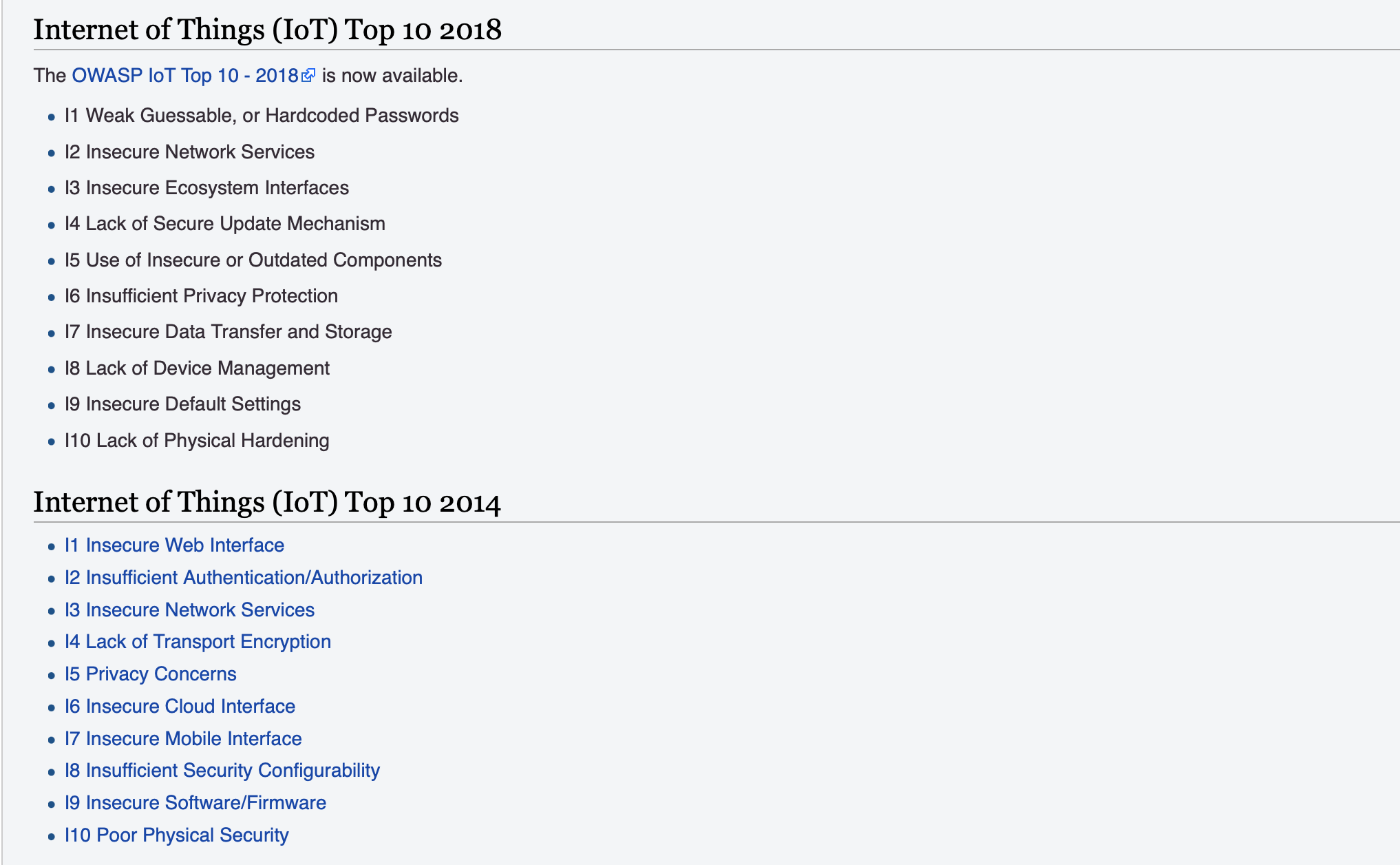
Tools
- fireware-mod-kit
From Teacher Alex’s PPT: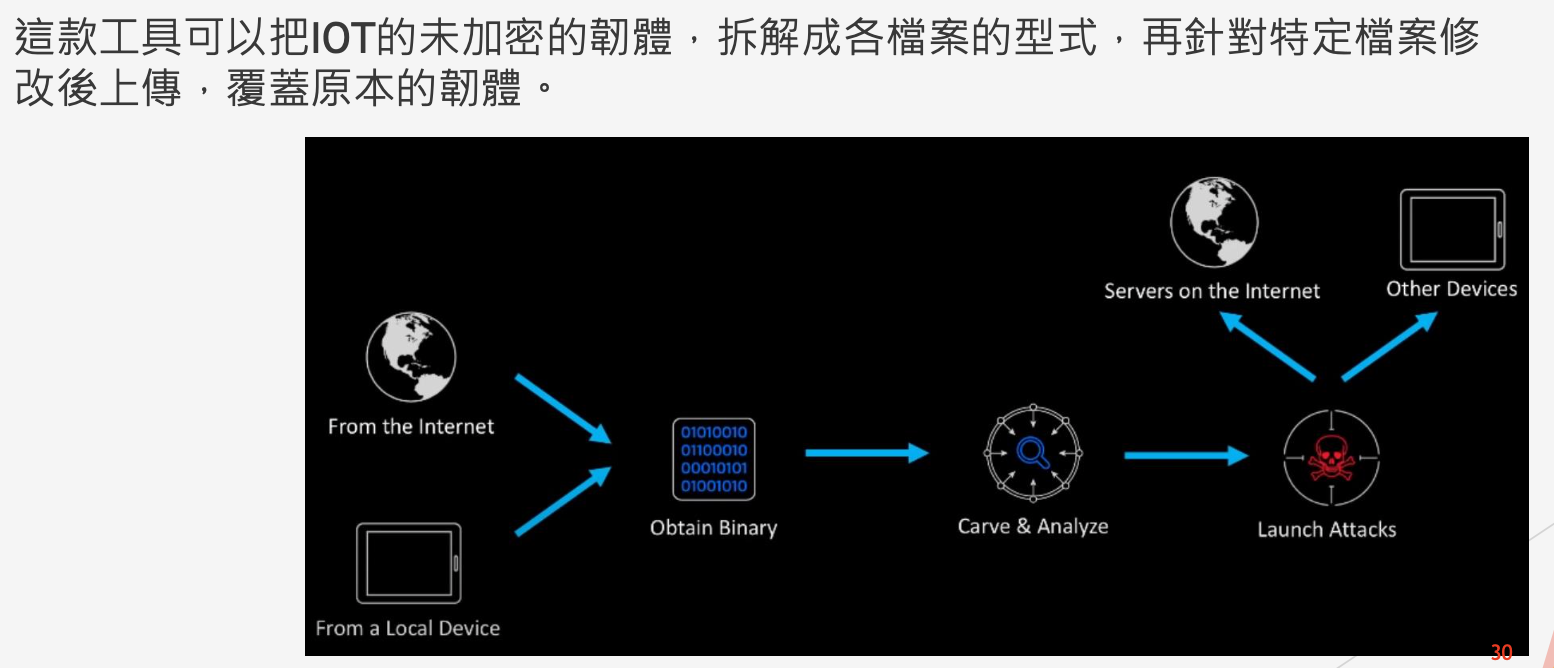
Kali provides buildin fireware-mod-kit.
Prevention
- Keep FW up-to-date
- Close necessary ports
- DO NOT use telnet
- Use encryption protocols such as SSL/TLS
- Enhance password strength
- Encrypt FW
- DO NOT use UPnP
🔸 Cloud Platform Hacking
OWASP Cloud Risk Top 10
From OWASP: https://owasp.org/www-pdf-archive/Cloud-Top10-Security-Risks.pdf
OWASP Cloud-Native Application Security Top 10
From OWASP: https://owasp.org/www-project-cloud-native-application-security-top-10/
Container Vulnerabilities
From Teacher Alex’s PPT:
- Impetuous Image Creation(未審視的映像檔)
- Unreliable Third-Party Resources(不可靠的第三方資源)
- Unauthorized Access(未經授權的存取)
- Insecure Container Runtime Configurations (不安全的容器設定檔)
- Data Exposure in Docker Files(Docker中的檔案遭暴露)
- Embedded Malware(嵌入式的惡意程式)
- Non-Updated Images(未更新的映像檔)
- Hijacked Repository and Infected Resoreces (受劫持的映象檔儲存庫和資源)
- Hijacked Image Registry (受劫持的映像註冊表)
- Exposed Service due to open port (開放的服務Port)
- Exploited Applications (利用應用程式的弱點)
- Mixing of Workload(混合再一起的應用容器)
- Mixing of Workload Sensitivity Levels (敏感級別的容器和一般容器混合)
Security Settings
Container
From Teacher Alex’s PPT:
- 設定分配給容器的資源
- Container 不應該以root執行
- 挑選驗證過的Repo
- 映像檔原始碼審查
- 關閉不必要的容器的網路服務
Bucket
Teacher Alex mentioned that we must be careful with the S3 Identity and Access Management (IAM).
From Teacher Alex’s PPT:
若和 Bucket 連動 APP 具有 SSRF 的弱點,則可以嘗試枚舉執行個體中繼資料和使用者資料.
Can use duckduckgo.com to search s3 buckets via site:s3.amazonaws.com
Case study: Unrestricted File Upload at Apple.com
https://medium.com/@jonathanbouman/how-i-hacked-apple-com-unrestricted-file-upload-bcda047e27e3
Kubernetes
From Teacher Alex’s PPT:
- 關閉公開存取
- 實施存取權控管
- 加密 Kubernetes 金鑰
- 設定 Kubernetes 的存取控制器
- 設定 Kubernetes 的網路政策
- 設定容器的資安規則
- 分離敏感的工作負載
- 掃描容器映像
- 稽核日誌
- 更新最新的 Kubernetes版本
Kubernetes master
The Kubernetes master node is a critical component of a Kubernetes cluster, and it contains sensitive information about the configuration and operation of the cluster. Therefore, if a hacker gains access to the Kubernetes master node, they could potentially take control of the entire cluster and access or manipulate data and resources.
Can use Shodan to find Kubernetes masters.
Tools
Trivy (Open source)
https://github.com/aquasecurity/trivy
From trivy github: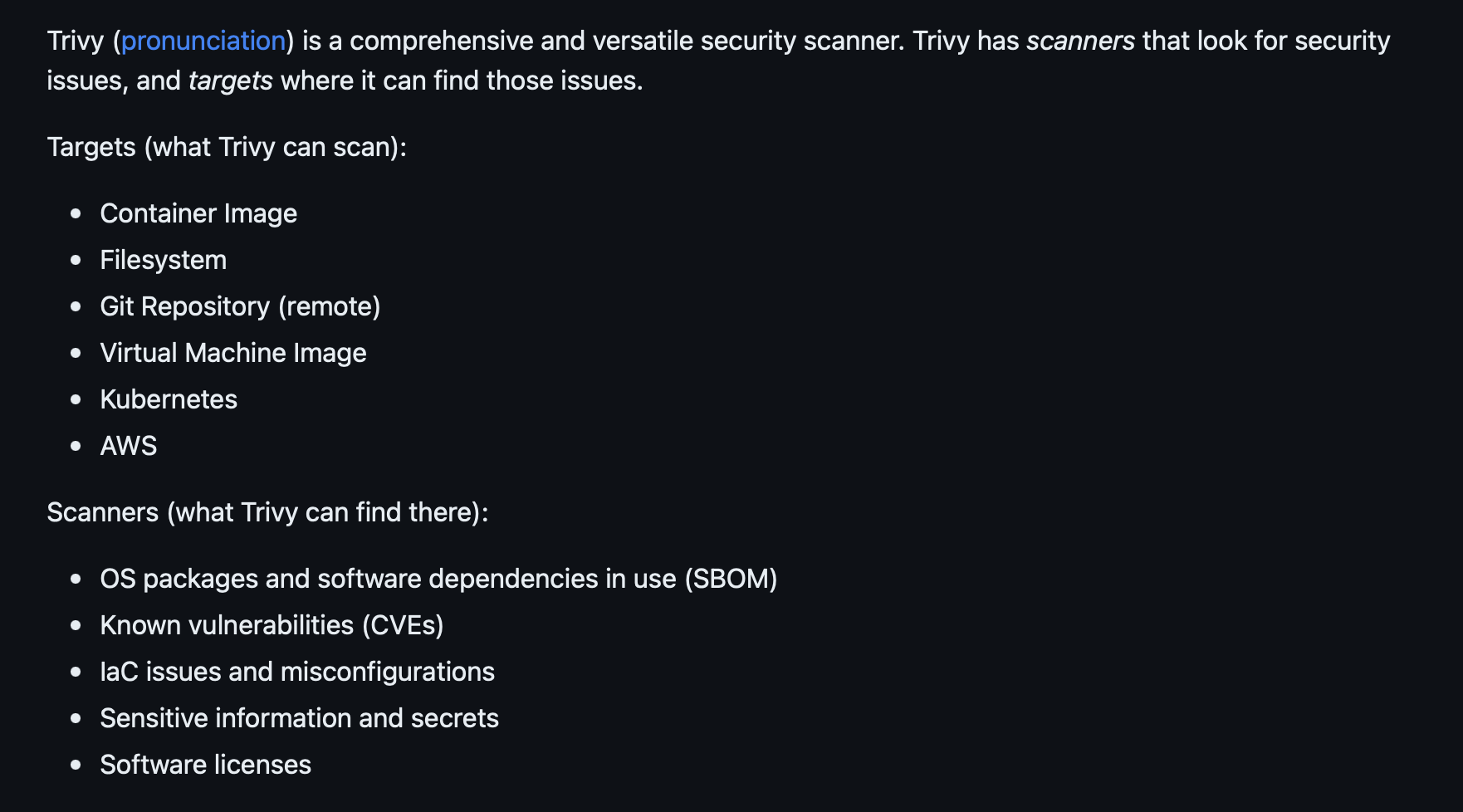
Sysdig (Paid tool)
https://sysdig.com
From Teacher Alex’s PPT: 針對大量部屬的容器、Image、Kubernets Contoller 等安全性掃描Nimbostratus (Open source)
https://github.com/andresriancho/nimbostratus
Same author who also created w3af: https://github.com/andresriancho/w3afs3-inspector (Open source)
Check AWS S3 bucket permissions.
https://github.com/clario-tech/s3-inspectorKube-hunter (Open source)
Check security weaknesses in Kubernetes clusters.
https://github.com/aquasecurity/kube-hunter