道德駭客實務入門-4/15課程筆記
TibaMe: 道德駭客實務入門及CEH認證班
Teacher: 林煌錡 (Alex Lin)
The class on 4/15 introduced session hijacking, malware, denial of service attack, and defense related items.
🔸 Session hijacking
Wiki: https://en.wikipedia.org/wiki/Session_hijacking
OWASP: https://owasp.org/www-community/attacks/Session_hijacking_attack
Session hijacking is a type of cyber attack where an attacker gains control of a user’s session in order to perform unauthorized actions. This can be done at both the network layer and the application layer.
Application layer
At the application layer, session hijacking involves stealing the user’s session cookie, which is used by the application to identify the user. Once the attacker has the session cookie, they can use it to impersonate the user and perform actions on their behalf.
Network layer
At the network layer, session hijacking involves intercepting packets between the client and server, and then impersonating the client to the server. The attacker can then inject their own packets into the session, and use them to perform actions as if they were the legitimate user.
Tools
- Burp Suite
- Owasp ZAP
- Wireshark
Prevention
https://stackoverflow.com/questions/22880/what-is-the-best-way-to-prevent-session-hijacking
- DO NOT pass session ID as URL parameter
- Set HttpOnly to true to prevent javascript to access the session cookie
- Use encryption protocols such as SSL/TLS
- Set session timeout
- Ask for the password for some important operations
🔸 Denial of Service attack (DoS)
A DoS attack is carried out by a single attacker or machine, with the goal of overwhelming the target server or network with traffic or requests, making it unavailable to legitimate users.
Wiki: https://en.wikipedia.org/wiki/Denial-of-service_attack
Distributed denial of service attacks (DDoS)
A DDoS attack is carried out by a network of compromised computers, known as a botnet, which are controlled by the attacker. The botnet is used to flood the target server or network with traffic or requests, making it impossible for legitimate users to access it.
Volumetric attacks
- Flood
- Amplification
- ICMP Flood
- UDP Flood
Protocol Attacks
- SYNC flood
- Fragmentation Attacks
- TCP-State-Exhaustion Attacks
- ACK flood
Application Layer Attacks
- Great Cannon
Wiki: https://en.wikipedia.org/wiki/Great_Cannon
Details: https://citizenlab.ca/2015/04/chinas-great-cannon/
Very powerful DDoS attacking tool owned by China government, which makes me really worried about the servers in Taiwan.
Tools
Slowloris
Script on github: https://github.com/gkbrk/slowloris
Haven’t tried the script. If it’s working, i think i can use this to perform a DoS test attack on the server.Botnet
A botnet is a network of compromised computers that are controlled by a cybercriminal or a group of cybercriminals for malicious purposes. These computers, also known as “bots” or “zombies,” are typically infected with malware that enables the attacker to remotely control them without the knowledge or consent of their owners.
From Teacher Alex’s PPT: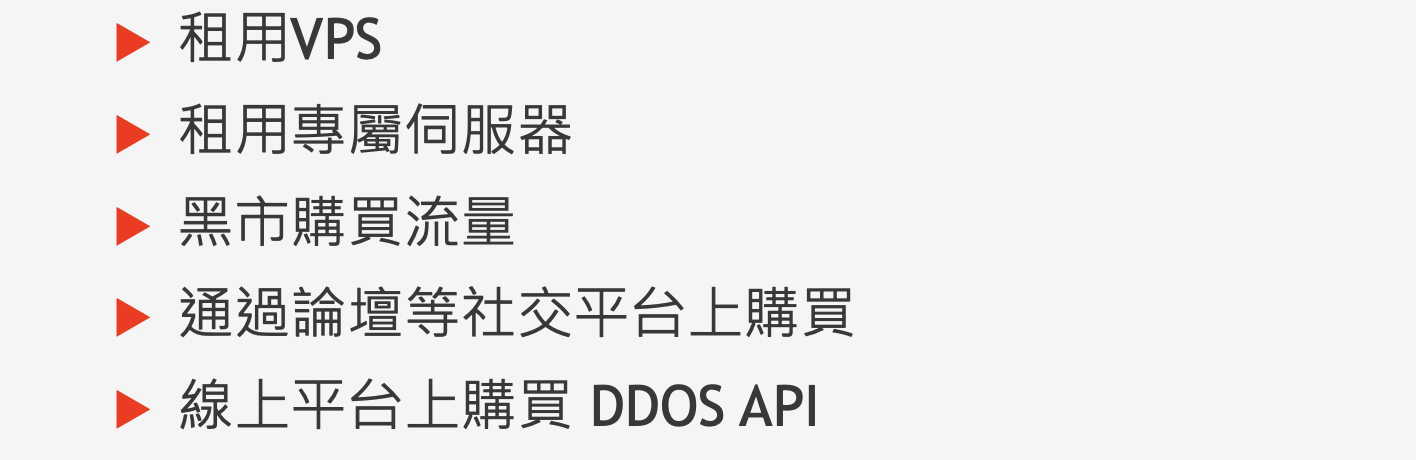
Others
DDoS is a powerful attack, and it can be carried out by individuals with minimal technical knowledge. While some of the most high-profile DDoS attacks have been carried out by hacktivist groups.
Recommend reading the news : https://technews.tw/2022/03/06/hackers-begin-weaponizing-tcp-middlebox-reflection-for-amplified-ddos-attacks/
More details regarding the cyber-attacks on Ukraine : https://www.europarl.europa.eu/RegData/etudes/BRIE/2022/733549/EPRS_BRI(2022)733549_EN.pdf
🔸 Malware
Advanced Persistent Threat (APT)
An Advanced Persistent Threat (APT) is a type of cyberattack in which an unauthorized user gains access to a system or network and remains undetected for an extended period of time. APT attacks are typically carried out by skilled and patient attackers who are motivated by political or financial gain. The goal of an APT attack is to gain access to sensitive data, and to maintain access to the system or network for as long as possible in order to achieve their objectives.
Wiki: https://en.wikipedia.org/wiki/Advanced_persistent_threat
https://ithelp.ithome.com.tw/articles/10188821
Trojan
- njRAT
- Poison ivy
- Necurs
- Rootkit Sirefef
- Emotet
- Glitch
- Zeus
- Mirai
Viruses & Worms
- EternalBlue
Fileless attack
A fileless attack is a type of cyber attack that does not rely on malware being downloaded and stored on a victim’s computer. Instead, it exploits vulnerabilities in the operating system or software applications to run malicious code in memory or abuse legitimate tools to carry out attacks. Because there is no file to detect and delete, fileless attacks can be harder to detect and mitigate than traditional malware-based attacks.
Wiki: https://en.wikipedia.org/wiki/Fileless_malware
From Microsoft:
https://learn.microsoft.com/zh-tw/microsoft-365/security/intelligence/fileless-threats?view=o365-worldwide
From Teacher Alex’s PPT: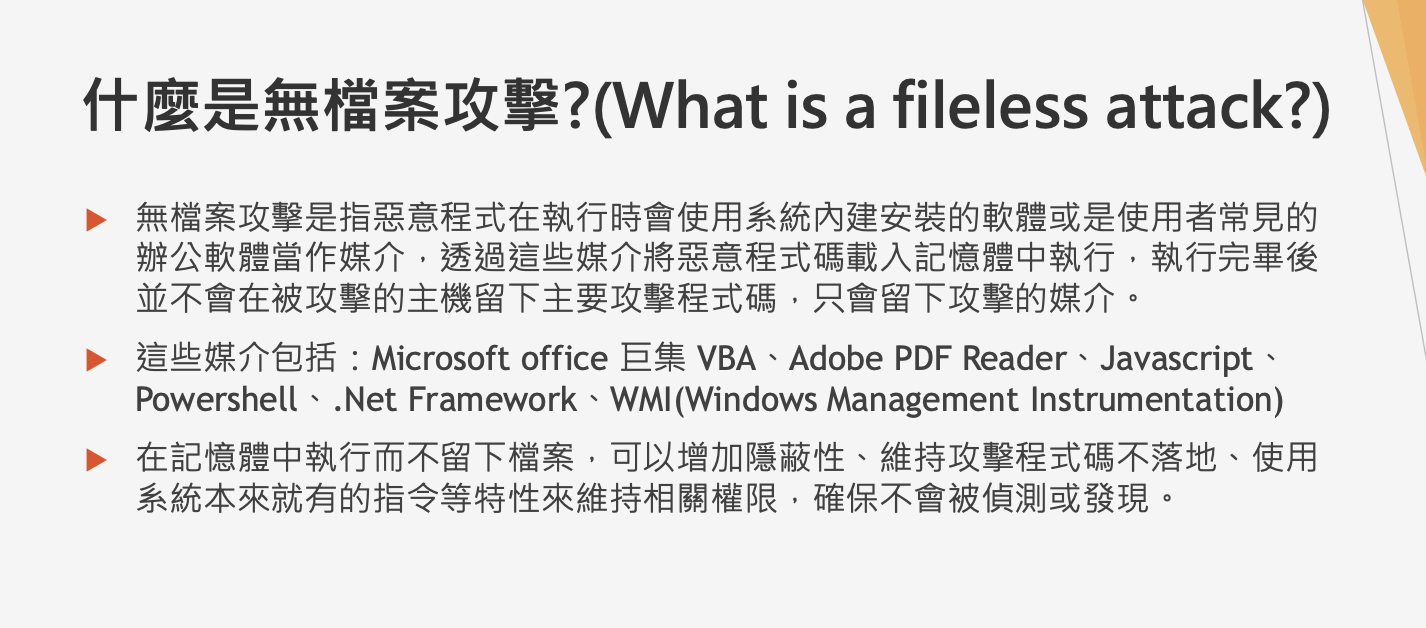
🔸 Defense
Intrusion Detection System (IDS)
IDS Wiki: https://en.wikipedia.org/wiki/Intrusion_detection_system
Tool: SNORT
https://zh.wikipedia.org/zh-tw/Snort
https://www.snort.org
Firewall
Firewall Wiki: https://en.wikipedia.org/wiki/Firewall_(computing)
Honeypot
Honeypot Wiki: https://en.wikipedia.org/wiki/Honeypot_(computing)
Can use Shodan to find Honeypot system, but some of them might be fake honeypots.
From Teacher Alex’s PPT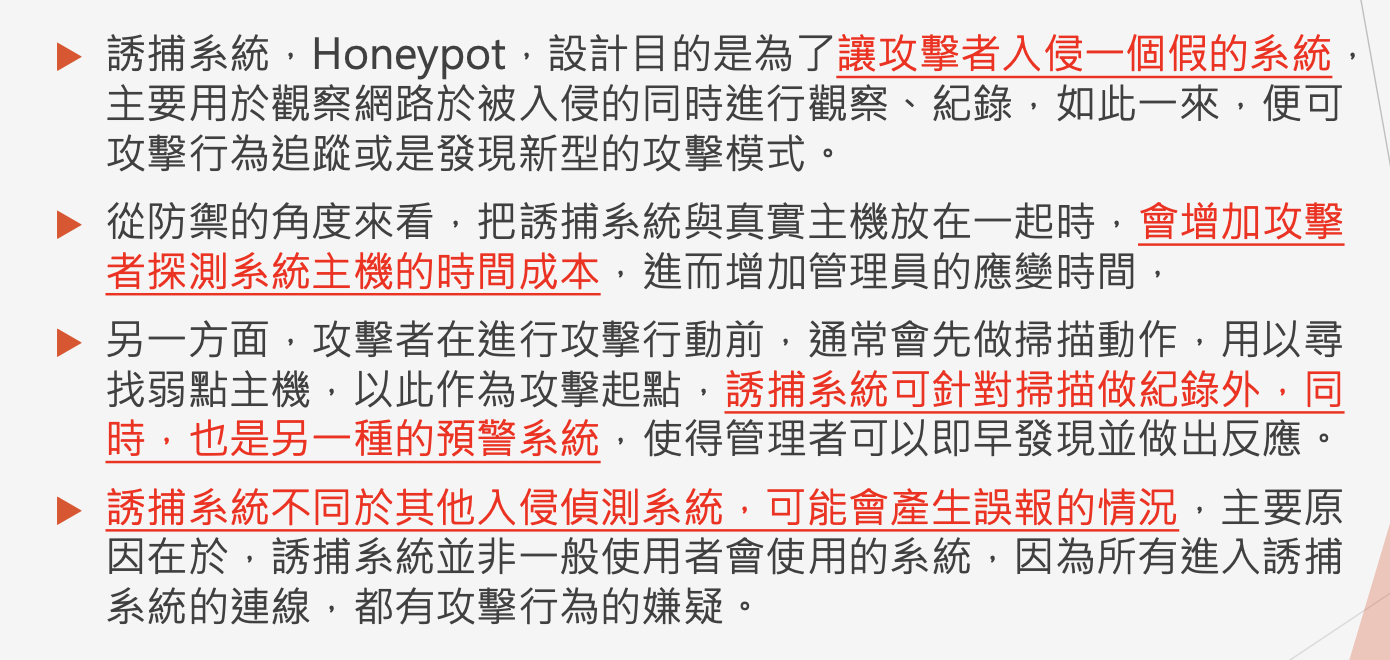
Evasion
NMAP: https://nmap.org/book/man-bypass-firewalls-ids.html
Intrusion Detection System Evasion
Wiki: https://en.wikipedia.org/wiki/Intrusion_detection_system_evasion_techniques
https://medium.com/@IamLucif3r/top-10-firewall-ids-evasion-techniques-cb1e1cc06f24
- Obfuscation. Can use Base64 encoding.
- False Negative
- Session splicing
- Unicode Bypass
- Packet Splitting
- Time To Live (TTL)
- Polymorphic Shell Code
- ASCII Shell Code
Firewall Evasion
- Firewalking
- Source Routing
- Tiny Fragments
- ICMP Tunneling
- Ack Tunneling
- HTTP / HTTPS Tunneling
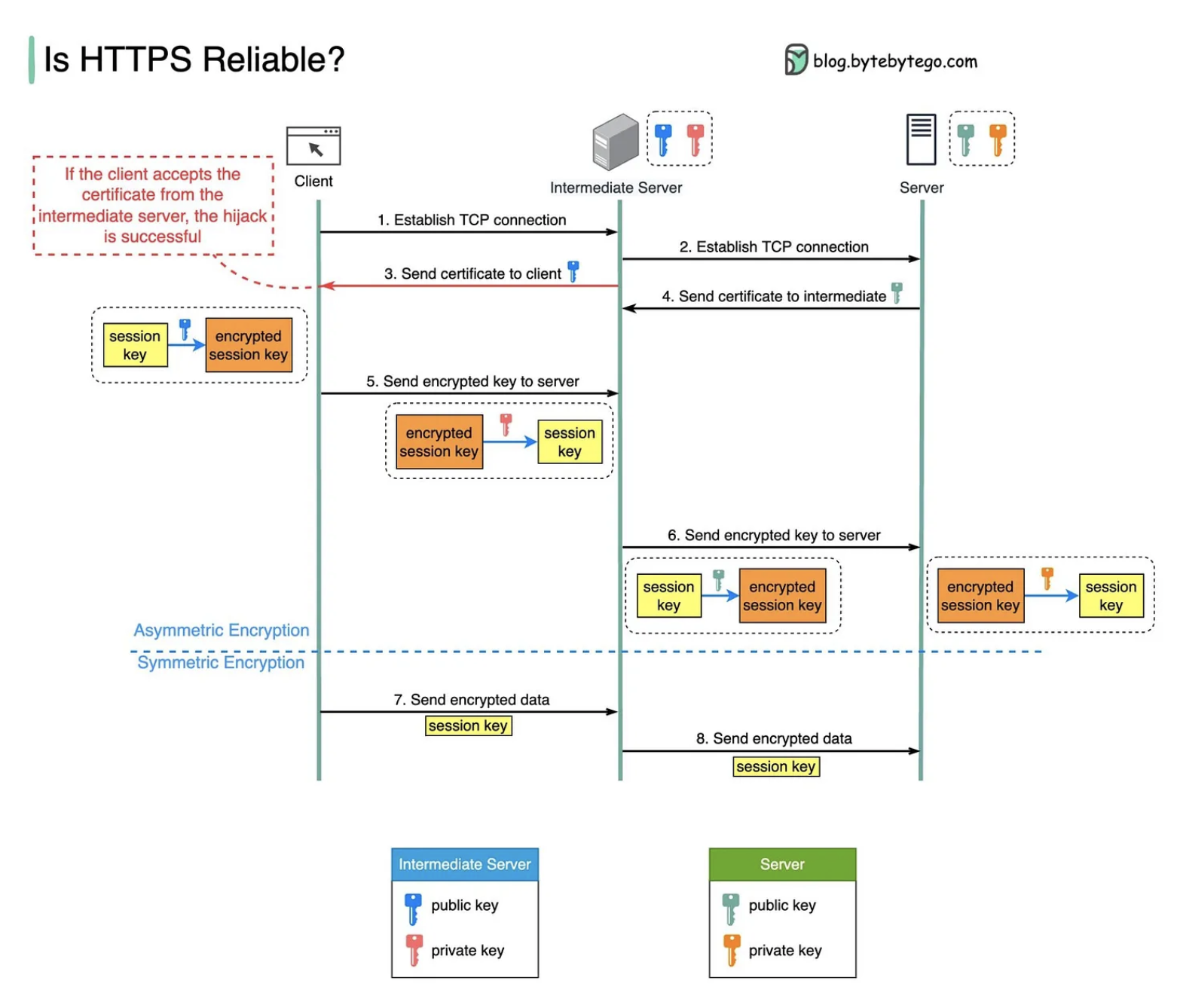
🔸 Recommend reading articles from Alex Xu’s https://blog.bytebytego.com
Password, Session, Cookie, Token, JWT, SSO, OAuth
https://blog.bytebytego.com/p/password-session-cookie-token-jwt
https://blog.bytebytego.com/p/ep34-session-cookie-jwt-token-sso
HTTPS & MitM attack
https://blog.bytebytego.com/p/how-does-https-work-episode-6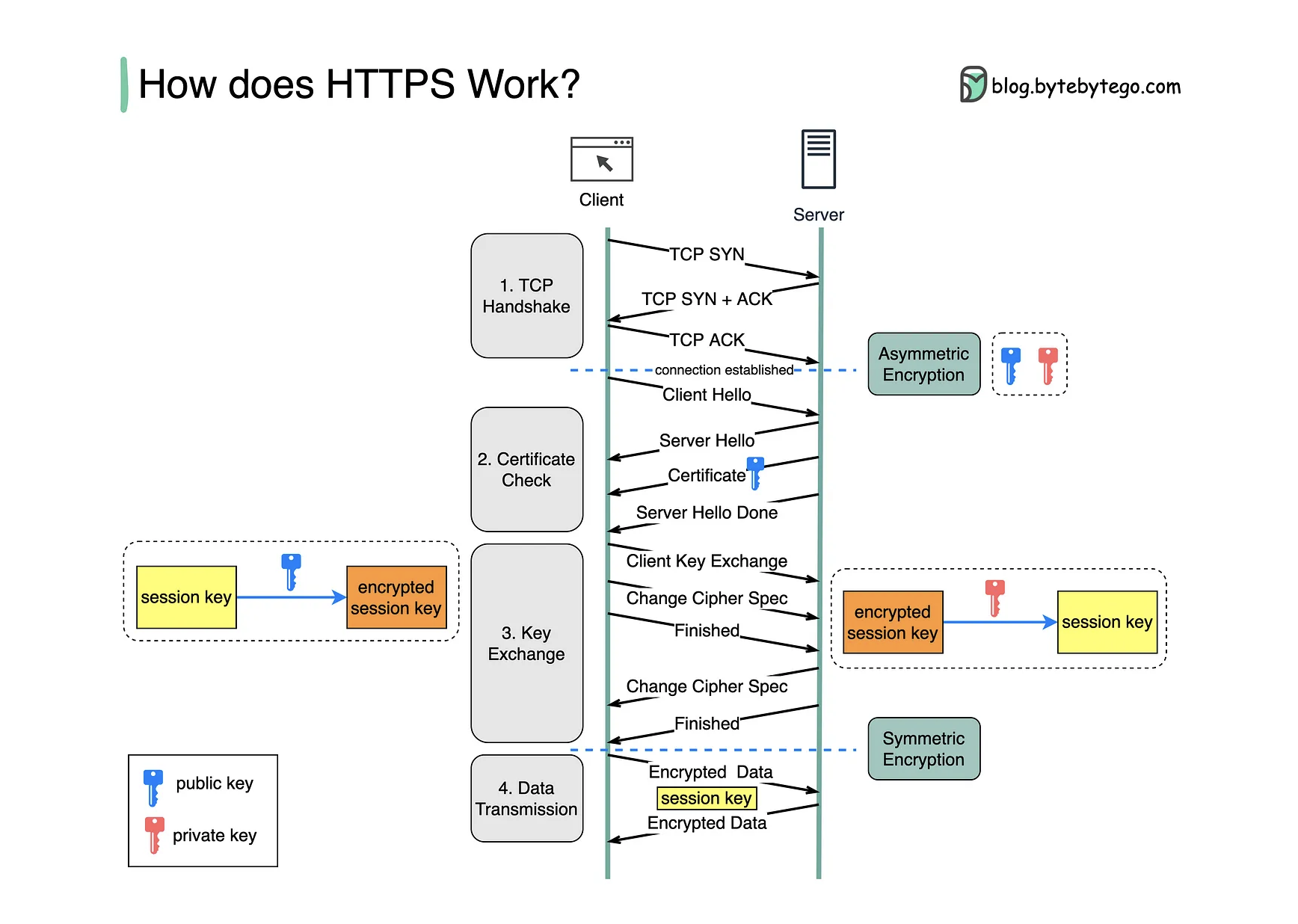
https://blog.bytebytego.com/p/ep21-is-https-safe-also