道德駭客實務入門-3/18課程筆記
TibaMe: 道德駭客實務入門及CEH認證班
Teacher: 林煌錡 (Alex Lin)
The class on 3/18 introduced general hacking concepts and focused on the reconnaissance (偵察) stage of hacking.
I am really interested in the reconnaissance (偵察) tools, most of which I have never heard of before.
Below are some tools introduced in the class.
Framework
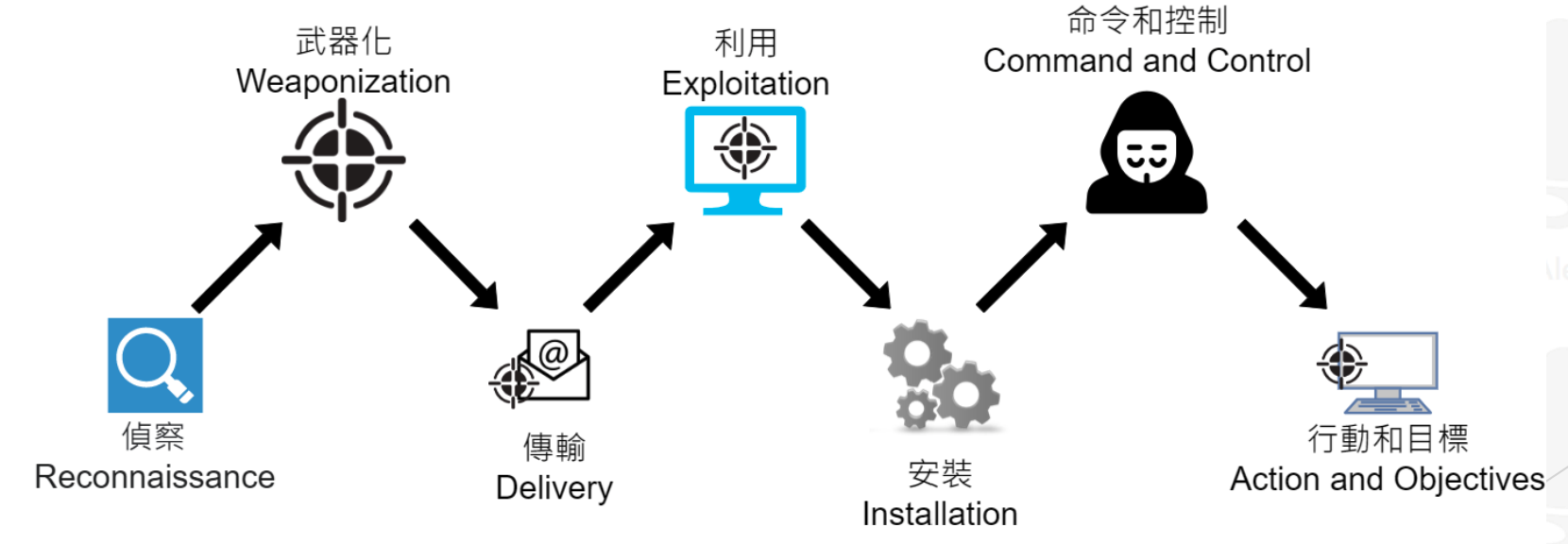
Cyber Kill Chain
- The image below is from Teacher Alex Lin‘s class PPT
ATT&CK
- ATT&CK Wiki
- Link: https://mitre-attack.github.io/attack-navigator/
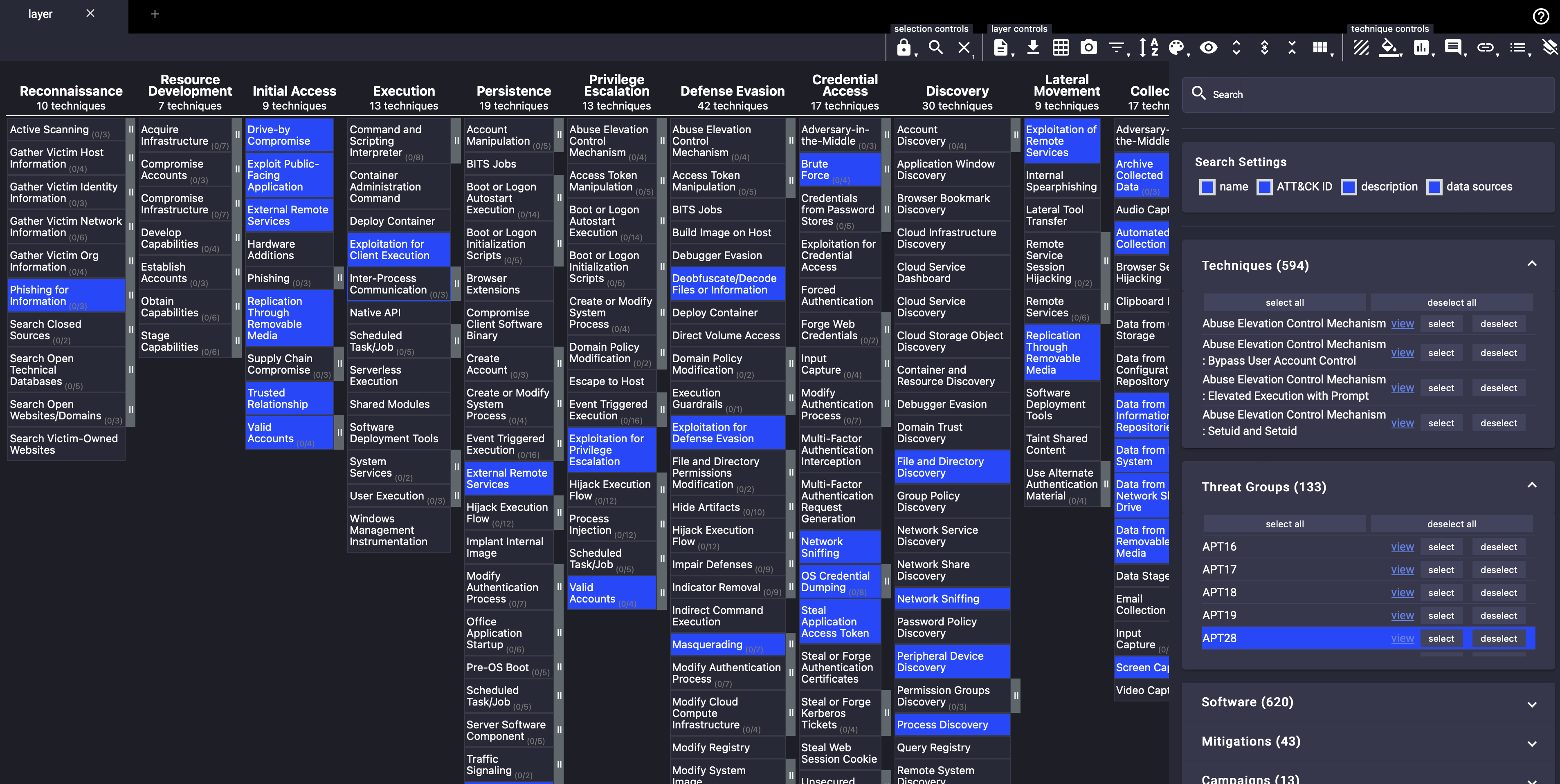
- There is an ID for each hacking technique. You can obtain details of each technique from https://attack.mitre.org/techniques/enterprise/[{"url":"/img/hacking-class/mitre-3.png","alt":""},{"url":"/img/hacking-class/mitre-4.png","alt":""}]
Reconnaissance Tools
偵察的目地主要是尋找目標。
Google Hacking
- Google Hacking Wiki
Google Hacking 意思是:熟悉Google search operators,你就有可能用Google找到適合攻擊的目標。 - Google Hacking Database
Google Hacking 指令集。 看了指令集才感嘆自己對Google大神了解太少。 - 可以使用robots.txt來阻止搜尋引擎來抓取內容。也看到有人說加了也不一定能擋。
https://developers.google.com/search/docs/crawling-indexing/robots/create-robots-txt?hl=zh-tw
DNS related tools
DNSdumpsters
https://dnsdumpster.com
輸入域名可以看見域名下所有的Server,和一些訊息, e.g. Web server used, on cloud or not.
輸入公司域名果然列出公司所有server。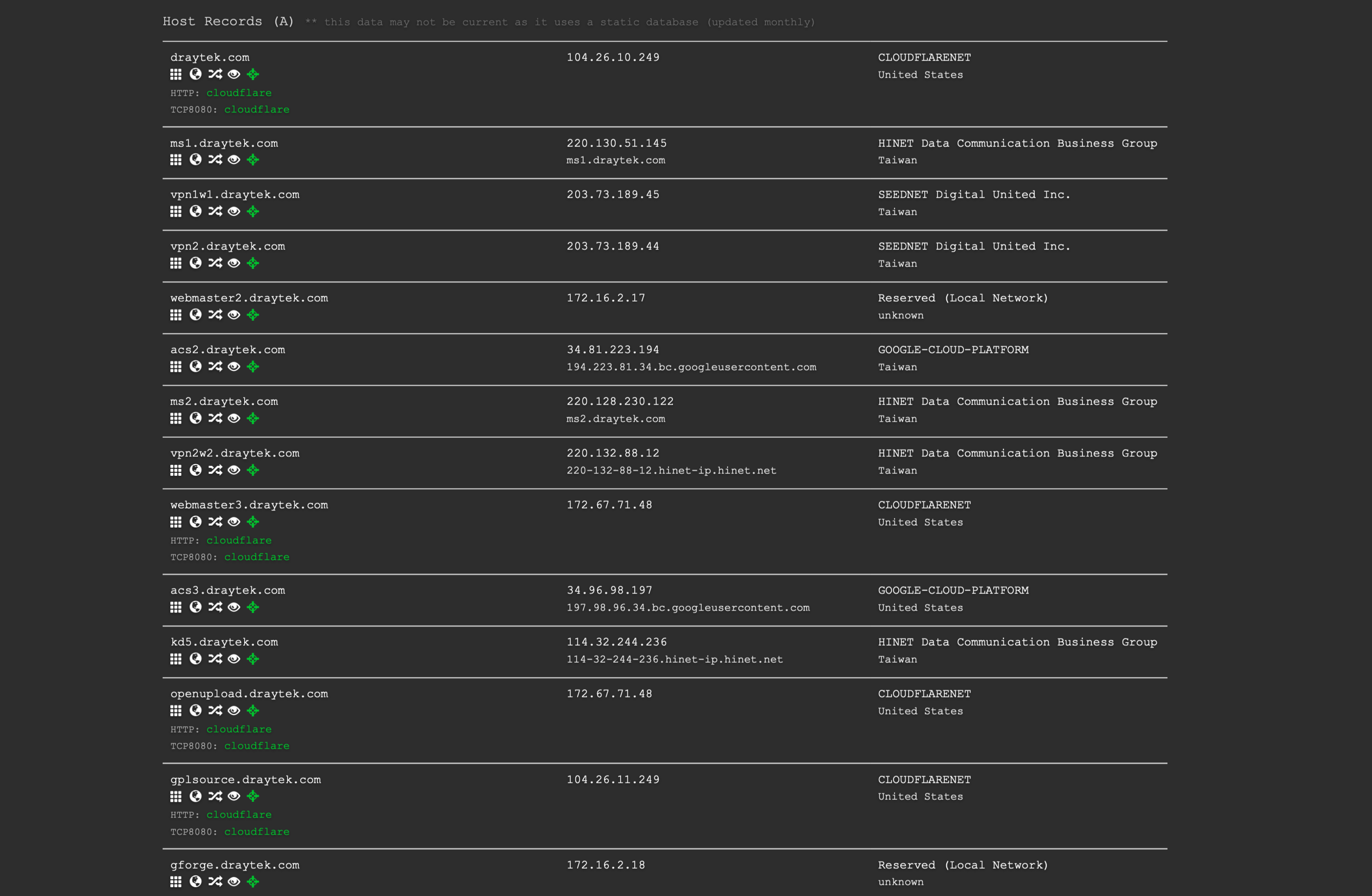
有完整的 Domain map.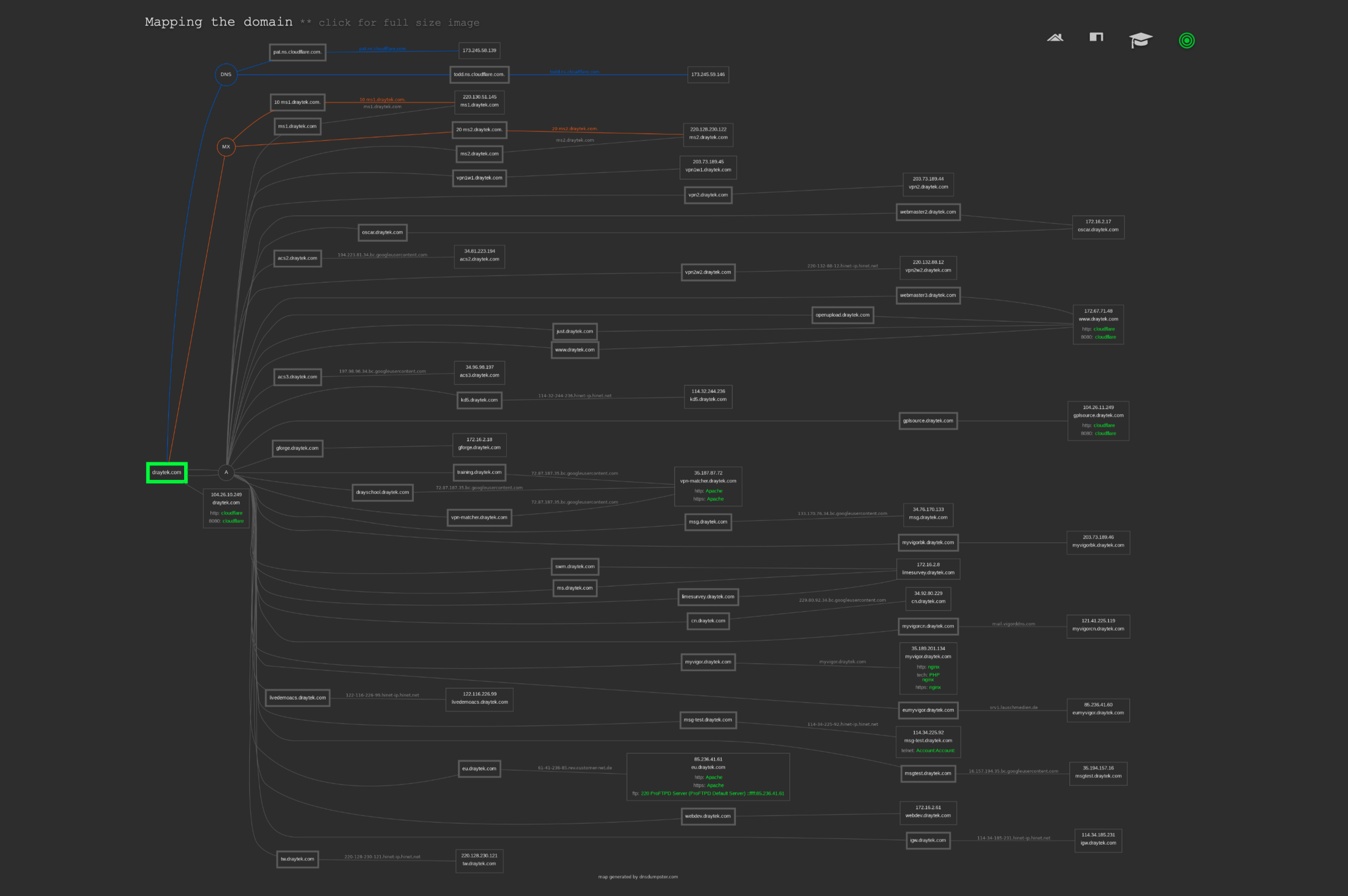
還可以對Server做port掃瞄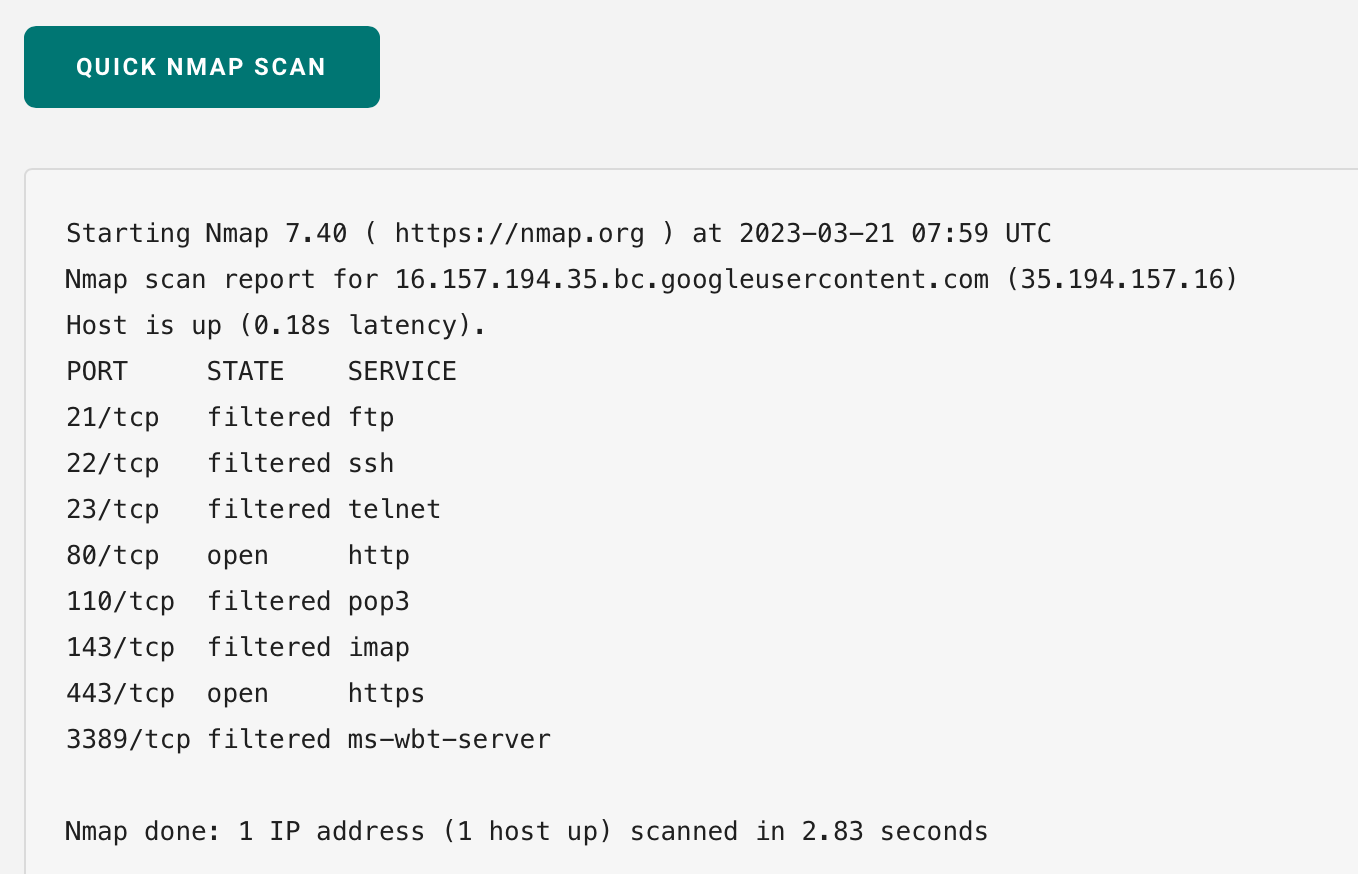
DNSrecon (Kali內建)
https://www.kali.org/tools/dnsrecon/Sbulist3r (Kali內建)
https://www.kali.org/tools/sublist3r/
Server analysis tools
- Netcraft
https://sitereport.netcraft.com
掃瞄Server找問題。
首先掃了自己的server看到一個risk,非常焦慮。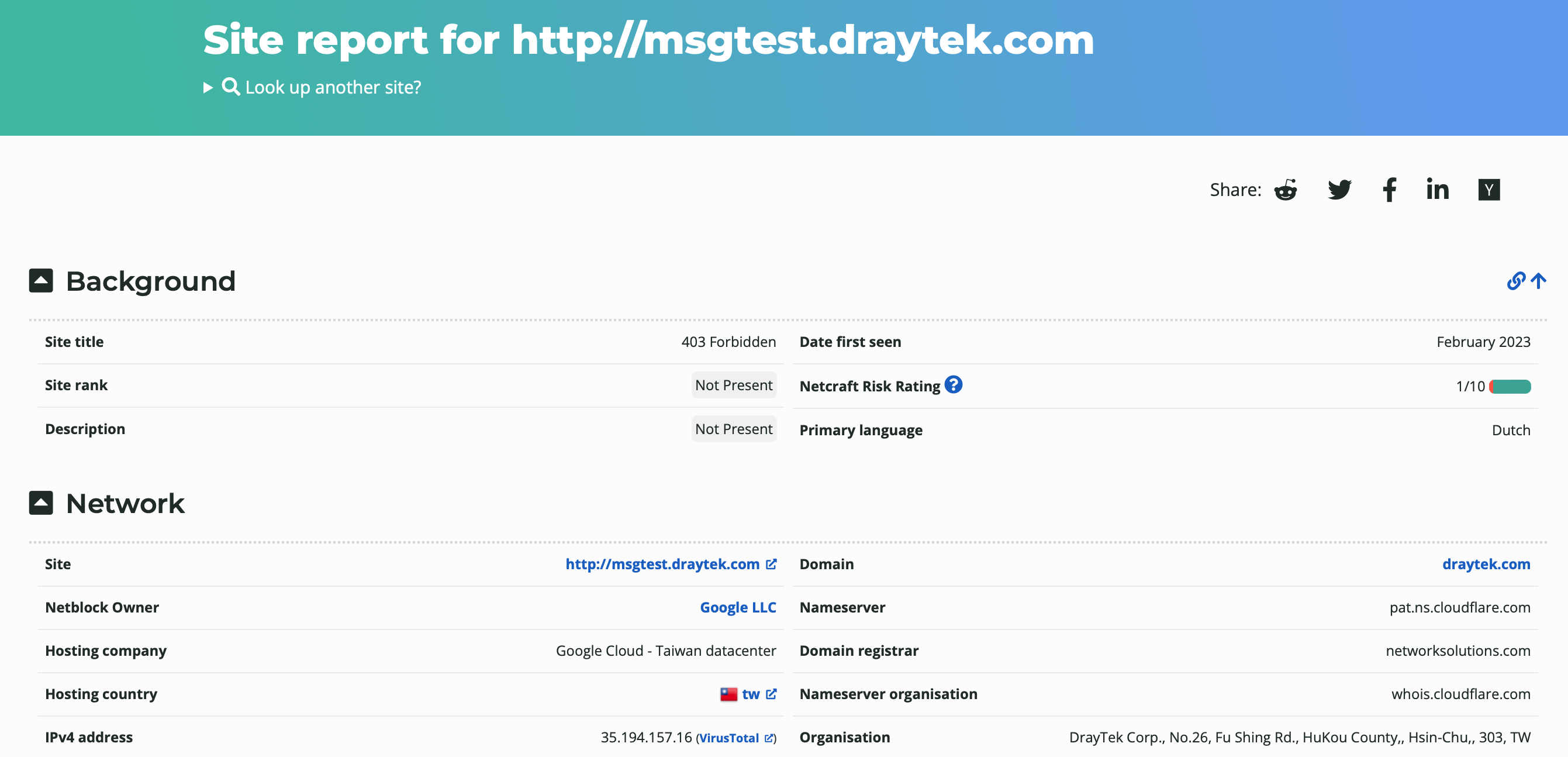
然後掃了公司的另幾台server看到一樣有一個risk,就不焦慮了。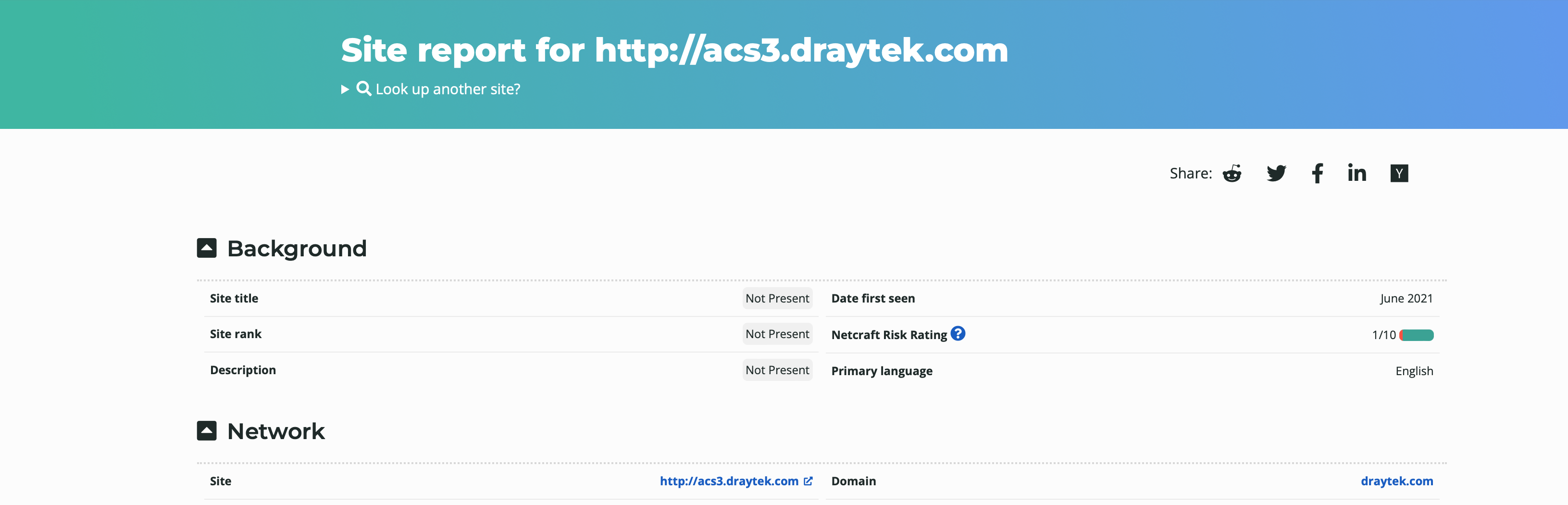
這個risk問題跟朋友討論後,覺的不是嚴重問題,之後會往討論的方向去嘗試改動。
又掃了公司的官網,看到Web Trackers,不能確定這是什麼。
後來查了一下,應該是網頁有加Google Analytics,是正常Tracker。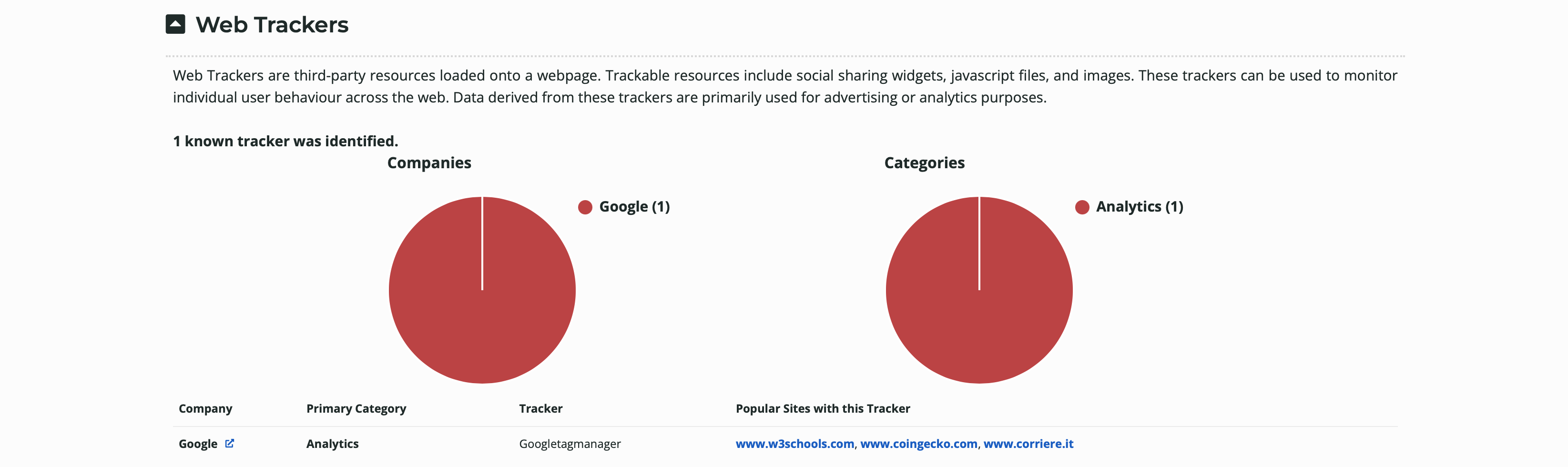
virtustotal
一樣掃瞄Server找問題。
https://www.virustotal.com/gui/home/url
用這個掃了自己的server是clean的。Whois
https://whois.domaintools.com
輸入域名可以看見完整的Domain profile。也可以從ip反查域名。[{"url":"/img/hacking-class/whois-1.png","alt":""},{"url":"/img/hacking-class/whois-2.png","alt":""}]Traceroute
我架的Server access不到,看到MIS用這個Command來抓問題。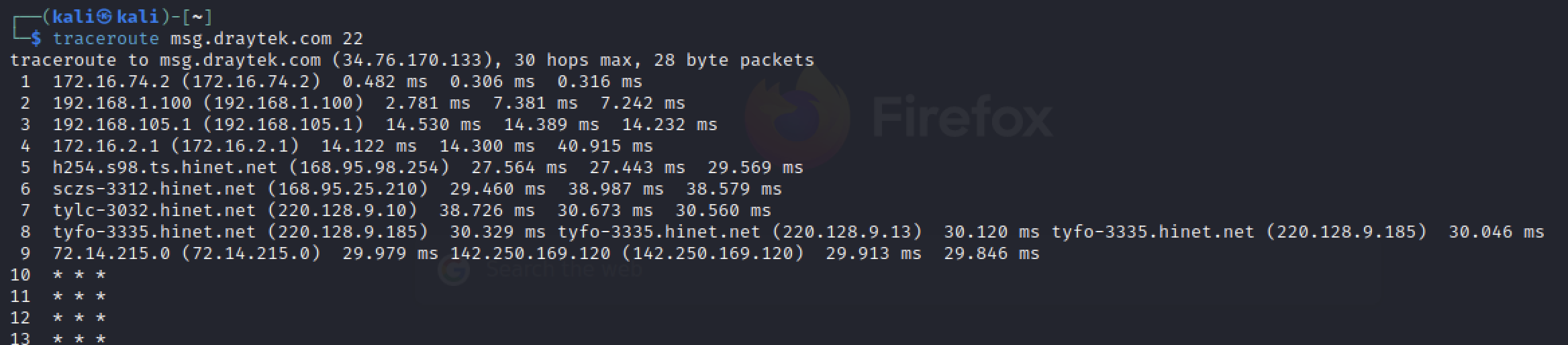
Service Search engine
Censys
https://search.censys.io
非常強大的服務搜尋引擎。我輸入公司名稱果然可以找到很多公司的router。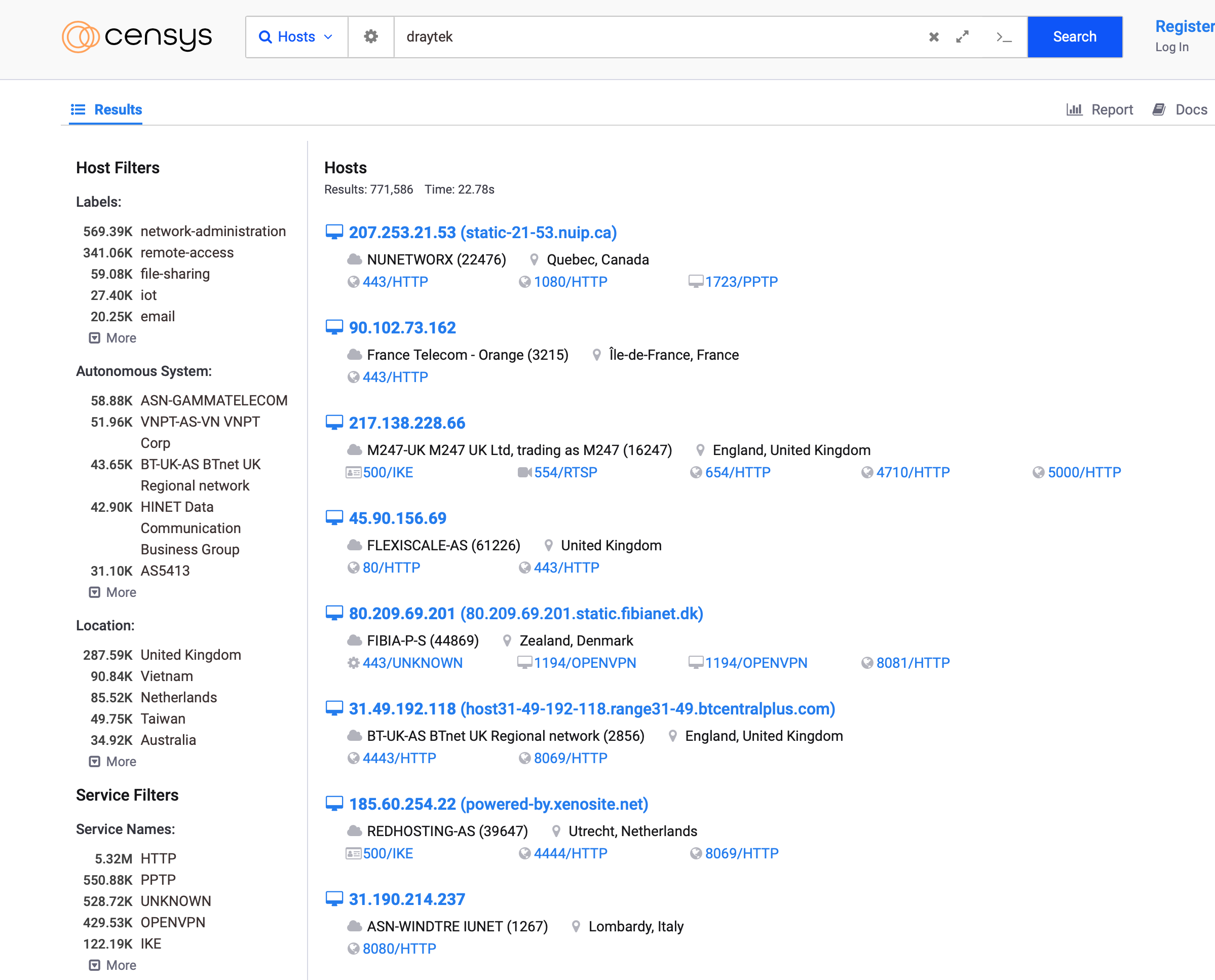
Shodan
比Censys更強大,可以分區域查找。可看訊息也更多。
https://www.shodan.io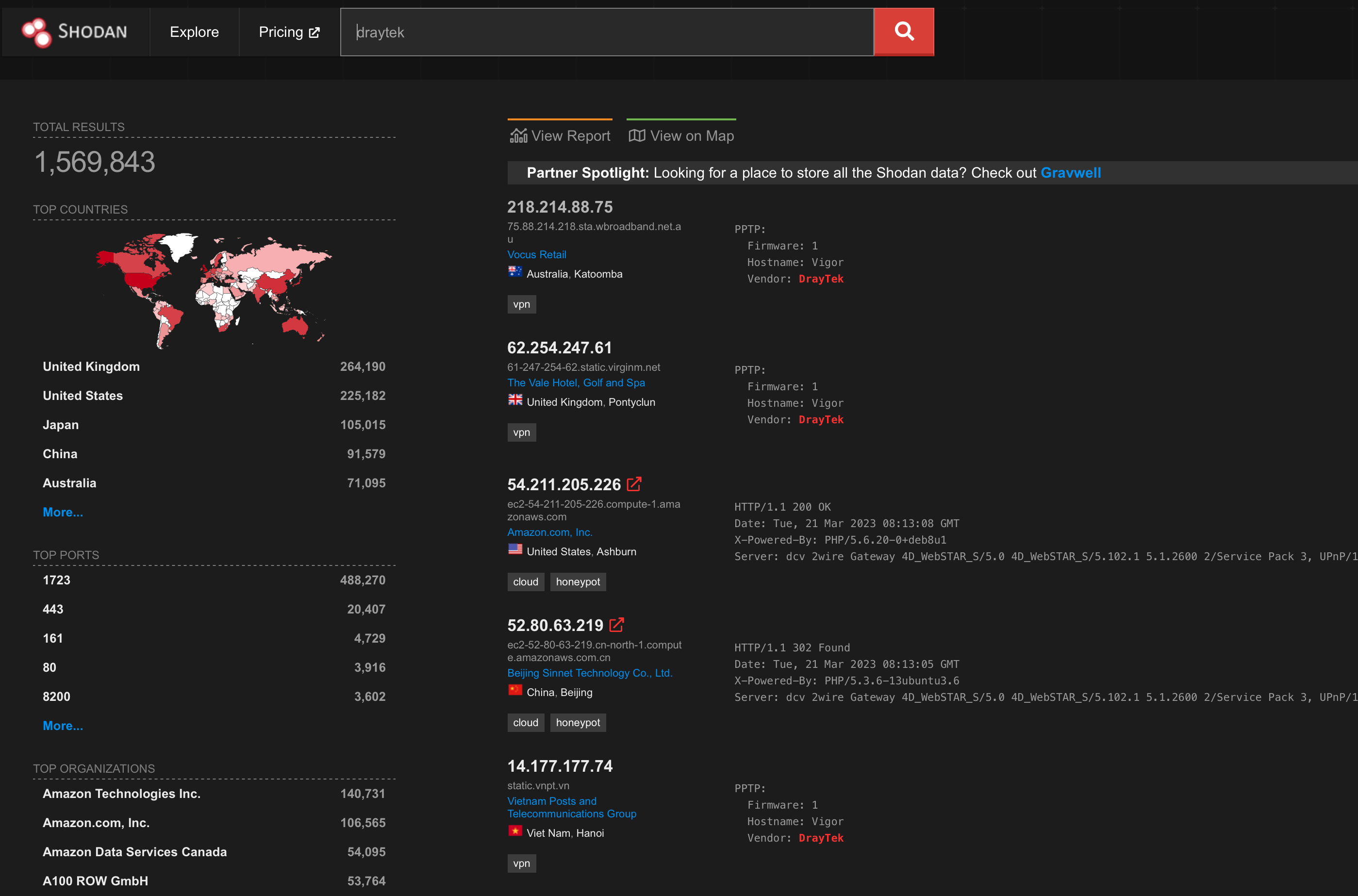
點進裝置還有所有Open Ports 和 Vulnerabilities!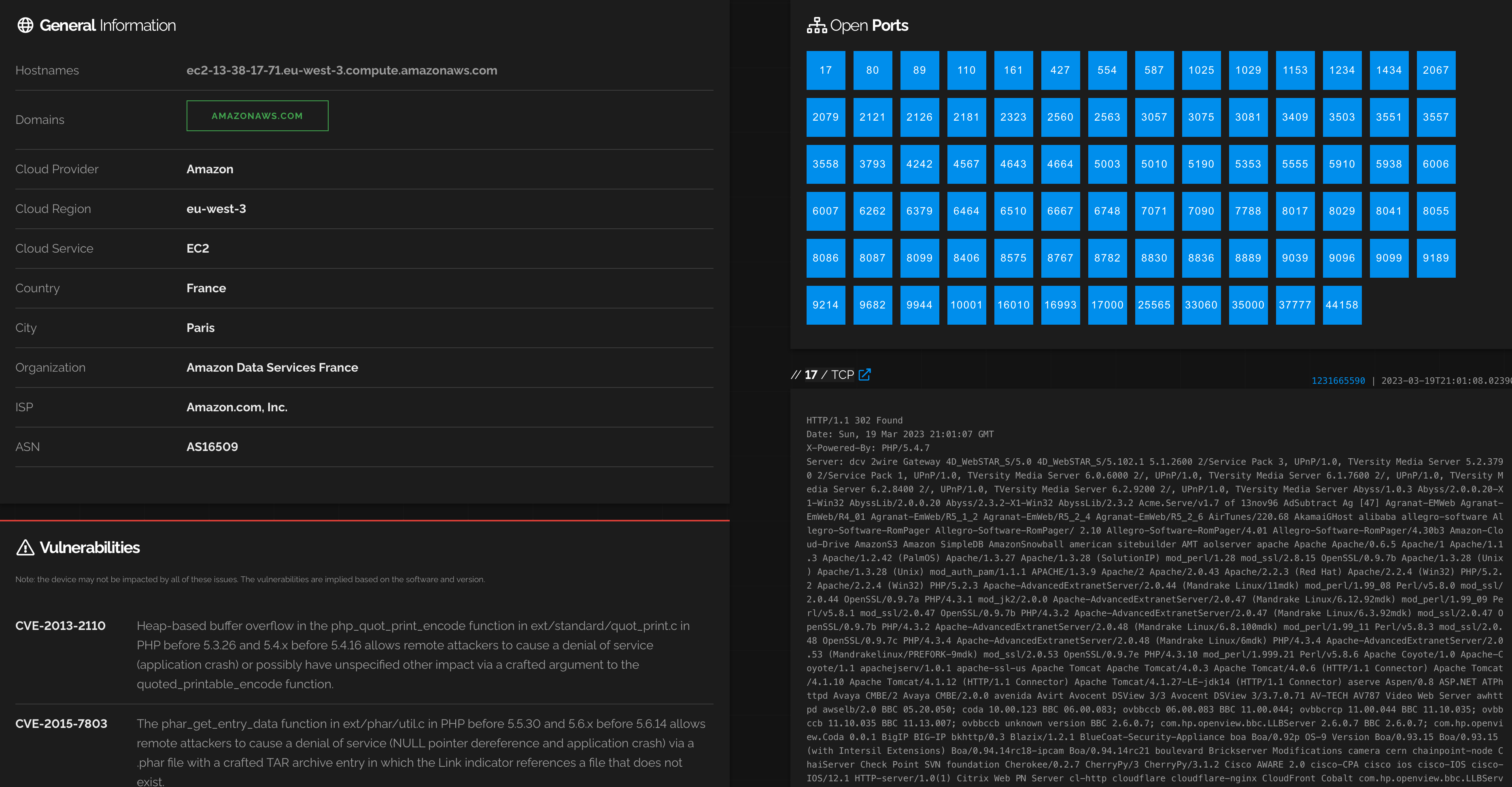
Fofa
https://en.fofa.info
可以針對某個漏洞去找有問題的Server.
比如,我查找台灣Server有log4j問題的,就列了一堆。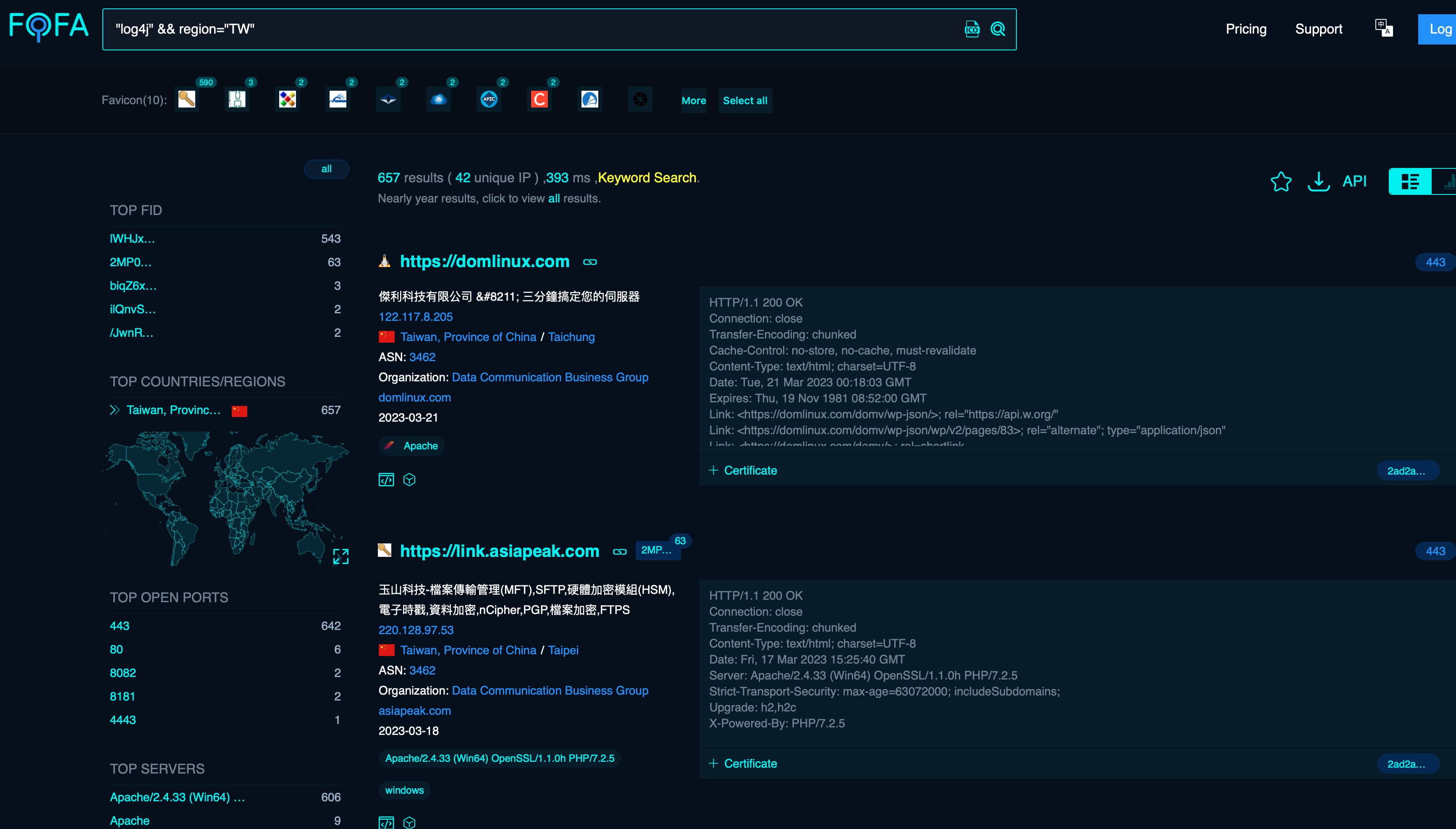
Shodan & Fofa更多精準搜尋推薦
https://tech-blog.cymetrics.io/posts/nick/shodan-fofa/
- ZoomEy
For China area
Web crawling tools
BurpSuite
https://portswigger.net/burpHTTrack
https://www.httrack.com/page/2/en/index.html
沒有實測,看了下面的文章,用HTTrack可以完整抓下整個網站內容。
https://www.minwt.com/webdesign-dev/html/15898.htmlWeb archive
http://web.archive.org
真是一個神奇的時光機器。完整紀錄了網站的歷史,有Snapshot。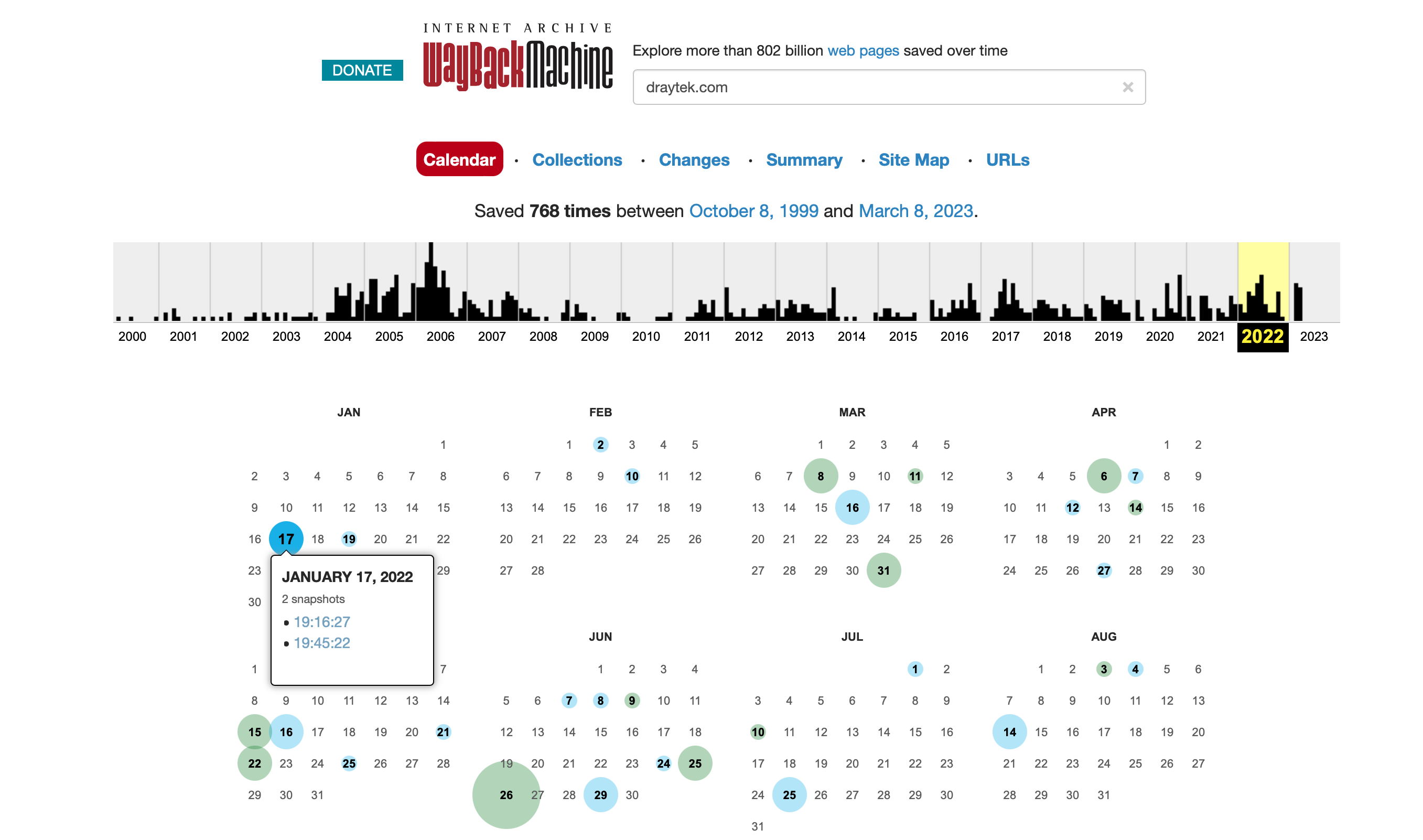
Octoparse
https://www.octoparse.com
抓取整個網站內容工具,要付費。ceWL (Kali內建)
https://www.kali.org/tools/cewl/metagoofil (Kali內建)
https://www.kali.org/tools/metagoofil/
Email analysis tools
從email中獲取各種訊息,比如說email伺服器地址。
theHarvester (Kali內建)
https://www.kali.org/tools/theharvester/infoga
Collect info. from social media tools
這個部分感覺主要用於尋找目標,蒐集訊息,先跳過好了。
Buzzsumo
Followerwonk
Sherlock
Social searcher
DarkWeb
Open-source intelligence (OSINT)
OSINT framework
這個網頁可以引導你去各種搜尋工具。
https://osintframework.com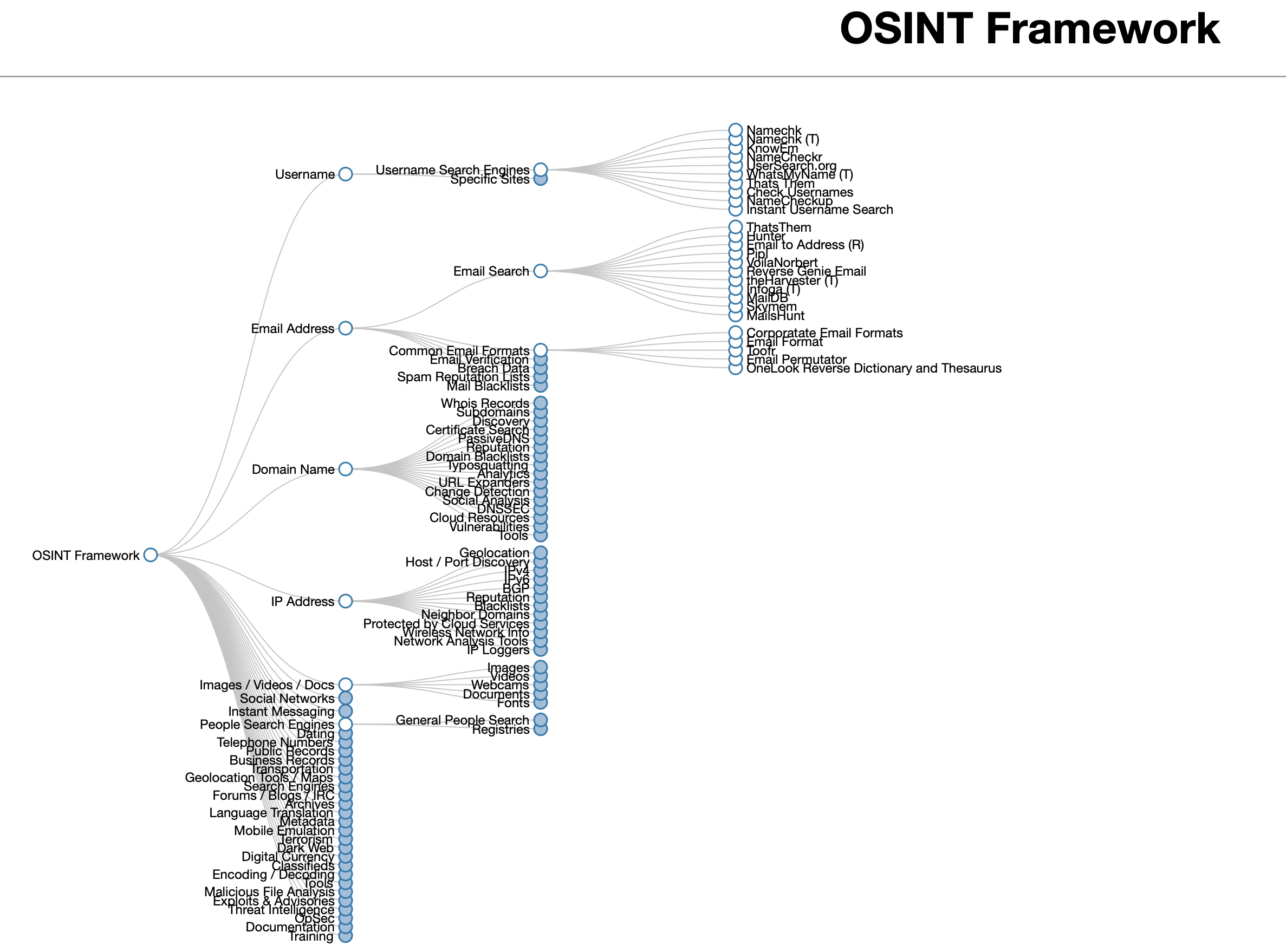
Maltego
https://www.maltego.com
屬於付費工具。Recon-ng (Kali內建)
https://www.kali.org/tools/recon-ng/Osrframework (Kali內建)
https://www.kali.org/tools/osrframework/
Network scan command line tools
以下command line tools都內建在Kali中。
NMAP
指令集:http://www.osslab.tw/books/linux-administration/page/nmap-常用指令集
NMAP也有提供圖形化介面工具。
Scan a host
1
2sudo nmap 192.168.1.1
sudo nmap -v 192.168.1.1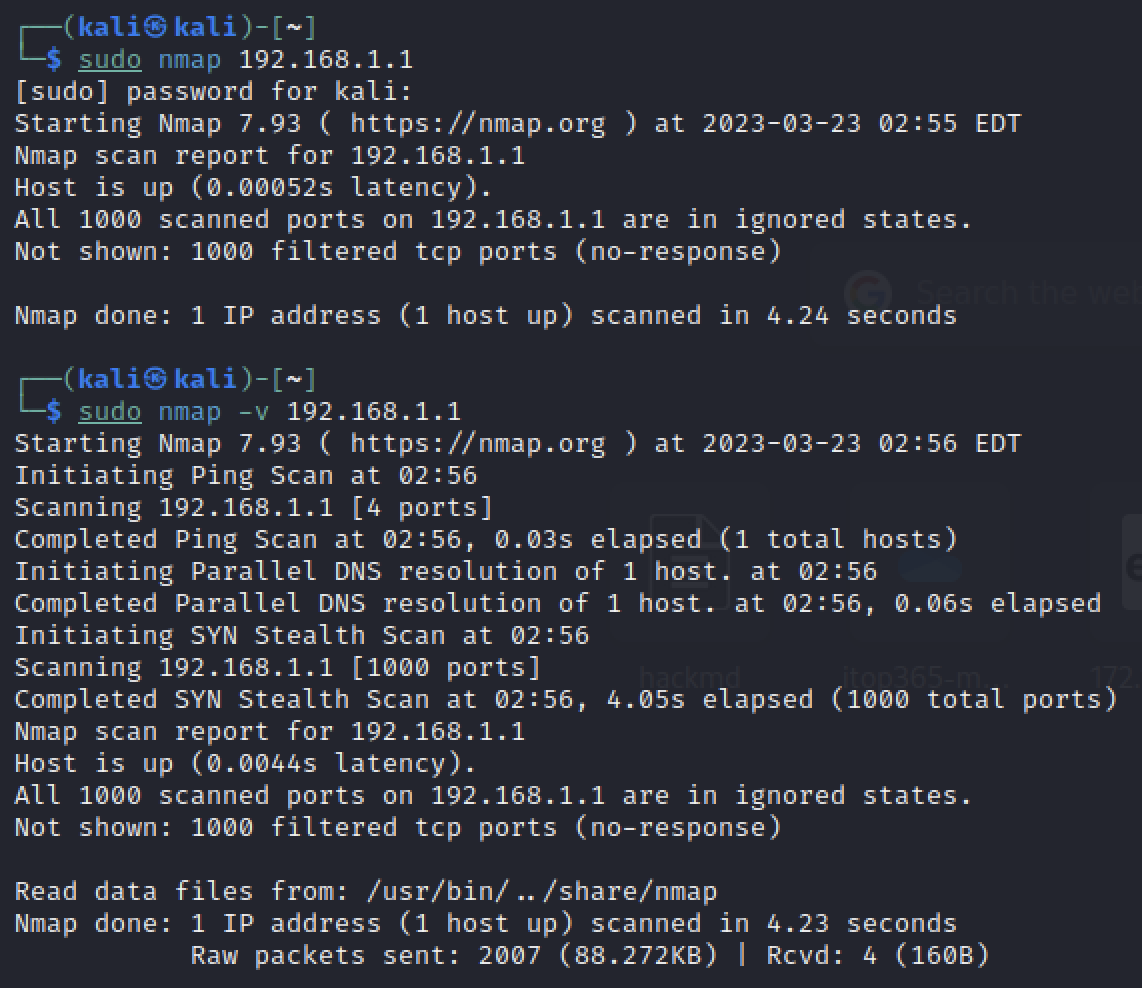
No response from these commands
1
2sudo nmap 192.168.105.0/24
sudo nmap -A 192.168.105.2
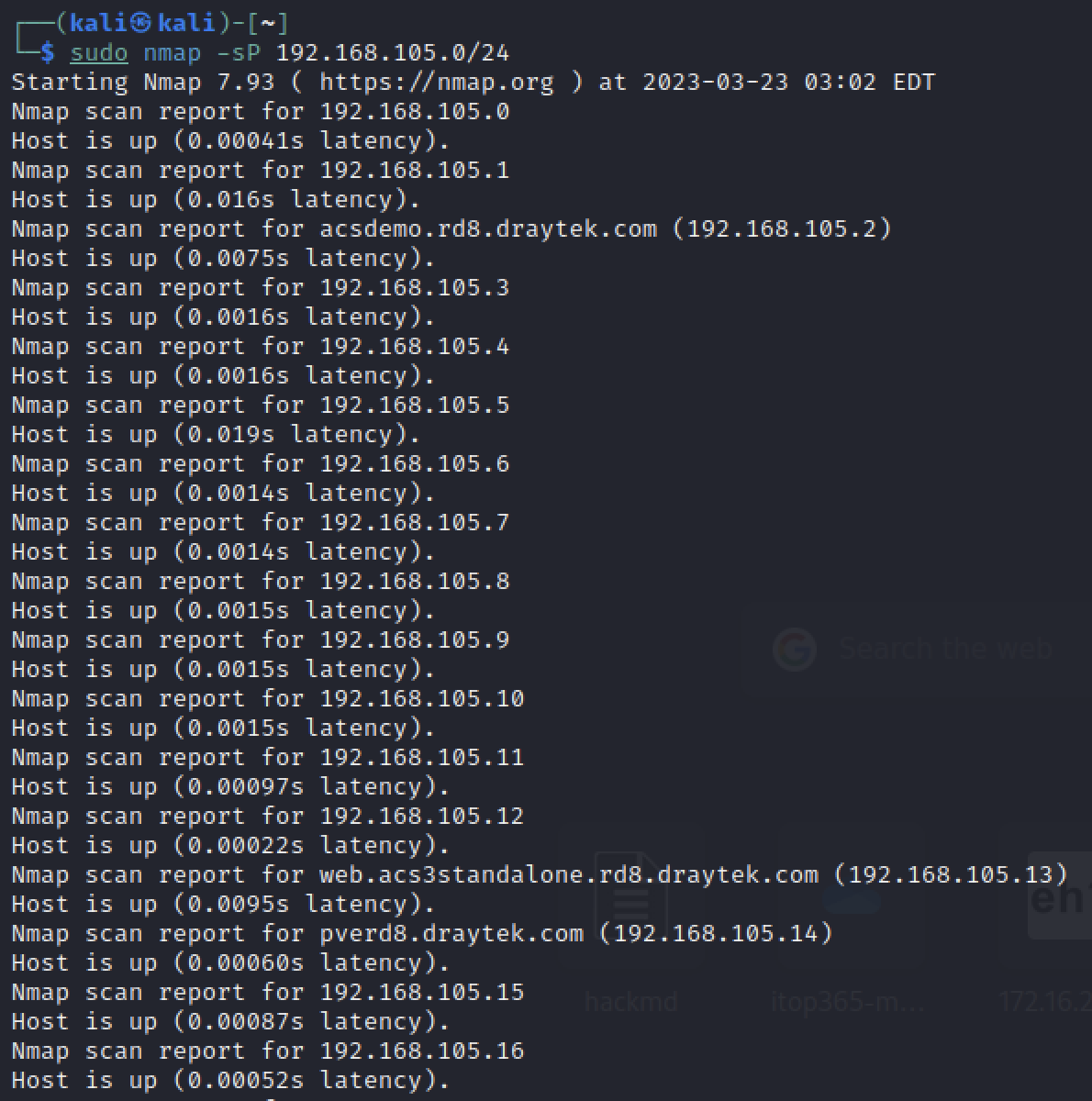
Scan host in a range
1
sudo nmap -sP 192.168.105.0/24
Scan host ports
1
2
3sudo nmap --top-ports 10 192.168.105.2
sudo nmap --top-ports 10 192.168.105.0/24
sudo nmap -PN 192.168.105.2[{"url":"/img/hacking-class/nmap-4.png","alt":""},{"url":"/img/hacking-class/nmap-5.png","alt":""},{"url":"/img/hacking-class/nmap-6.png","alt":""}]nmap -v -sV –script=nfs-showmount 192.168.105.2
[{"url":"/img/hacking-class/nmap-7.png","alt":""},{"url":"/img/hacking-class/nmap-8.png","alt":""},{"url":"/img/hacking-class/nmap-9.png","alt":""}]
HPING3
1 | sudo hping3 -A 192.168.105.2 -p 443 |
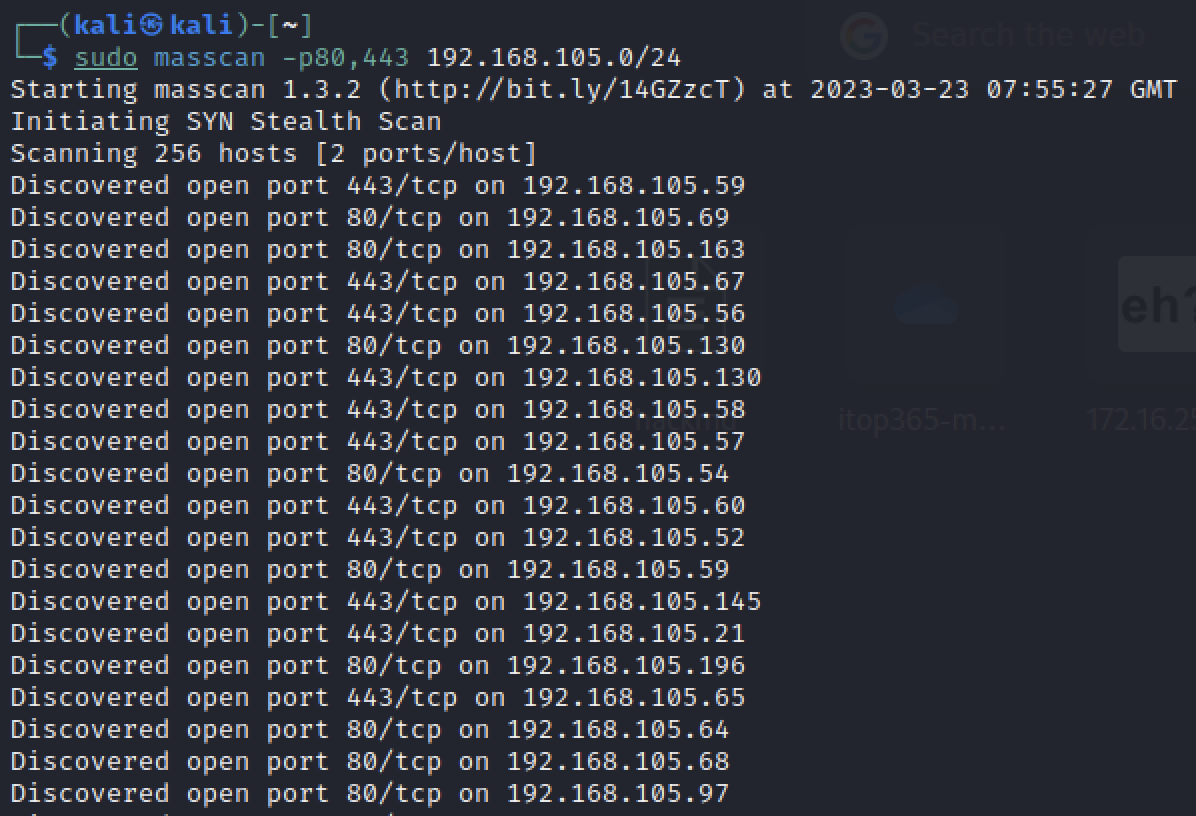
massscan
1 | sudo masscan -p80,443 192.168.105.0/24 |
Host scan
主機掃描目地主要是針對選定目標收集更多資訊。
ARP scan
1 | sudo nmap -sn -PR 192.168.11.0/24 |
UDP scan
1 | sudo nmap -sn -PU -Pn 192.168.105.193 |
ICMP scan
1 | sudo nmap -sn --disable-arp-ping -PE 192.168.1.0/24 |
TCP scan
1 | sudo nmap --disable-arp-ping -sT 192.168.105.193 -p 445 |
SCTP scan
1 | sudo nmap --disable-arp- ping -sY 192.168.105.193 -p 10000 |
OS fingerprint
TTL長度辯識OS
Linux -> 64
Windows -> 128
Solaris/AIX -> 254
nmap commands
1 | sudo nmap -Pn --disable-arp-ping -O 192.168.105.2 |
Scan bypass IDS & firewall
封包分段(Packet Fragmentation)
1 | ping -l 1473 192.168.1.x |
通訊埠來源修改(Source Port Manipulation)
1 | sudo nmap -g 80 -p 445 192.168.1.250 |
IP 位址誘餌(IP Decoy)
1 | sudo nmap -D RND:10 192.168.1.250 |
IP 位址欺騙(IP Spoofing)
1 | sudo nmap -e eth1 --disable-arp -Pn -S 192.168.40.5 -p 445 192.168.1.250 |